5. Complexity and Weapons of Mass Destruction in Northeast Asia
© 2015 Peter Hayes and Roger Cavazos , CC BY 4.0 http://dx.doi.org/10.11647/OBP.0059.05
This chapter examines the increasingly complex problem of the threat posed by nuclear weapons of mass destruction (WMD) in Northeast Asia. The first section sketches the recent evolution of the role played by nuclear weapons in international affairs and provides a summary of the nuclear weapons problem both globally and regionally from a conventional, policy-oriented viewpoint. It argues that US nuclear hegemony was constructed to contain the contradictions at the core of its nuclear-based state security strategy.
The second section argues that bottom-up incremental changes due to nuclear weapons proliferation led to tipping points whereby the system of US nuclear hegemony was transformed. The threat of nuclear war metamorphosed and metastasized from a Cold War-era “manageable” threat in Northeast Asia to a rapidly changing, turbulent, and uncontrolled “nuclear breakout” by the DPRK and potentially by non-state actors. In the third section, we note that this phase-shift in the nature of the nuclear weapons problem has led to a renewed and likely increased threat of nuclear next-use in the region. In the fourth section, we examine state-based strategies for solving the nuclear weapons problem, commonly framed as “arms control” or “disarmament” measures. We note that because these approaches do not attend to the underlying drivers of the bottom-up proliferation and increased risk of nuclear next-use, nor to the cross-cutting issues that exacerbate these dynamics, these conventional measures may stabilize, but not eliminate the twin nuclear threats associated with declining US nuclear hegemony, namely horizontal proliferation and increasing risk of nuclear war. Rather, as the chapter concludes, only civil society-based cooperative security strategies can supplant nuclear weapons and related insecurity from destabilizing the region.
Introduction
Since the end of the Cold War, the world in which nuclear weapons exist has changed dramatically. The basic elements of the global system into which nuclear weapons are interwoven include the following: (a) great powers with enormous superiority over most states due to their conventional and nuclear forces, that is, of the United States (and its allies), of Russia, and of China; (b) states locked into conflicts that are stabilized by defense-dominated deterrence and have no recourse to nuclear weapons, such as Taiwan and formerly North Korea; (c) states engaged in traditional nuclear and conventional high-risk standoffs based on deterrence by retaliatory threat with constant danger of preemption, such as Israel, India and Pakistan; and (d) states with no adversaries in sight and which are not driven to acquire defensive or offensive deterrent capabilities either directly or indirectly extended by others, such as New Zealand and Mexico.1
Consequently, nuclear weapons are now woven into international affairs in a more complicated and multi-dimensional fashion than during the Cold War. Four tributaries feed into this river of turbulent change, namely:
Trend 1: The triangular nuclear standoff between the United States and its nuclear allies in Asia and Europe, the former Soviet Union, and China has shifted to one of general deterrence rather than one aimed at sustaining immediate deterrence against the threat of pre-emptive attack. At the global level, nuclear weapons have receded into the “background” of great power politics and serve as hedging insurance against regression to confrontational postures by any one of these great powers against the others, whether because of domestic or external causes. This move away from imminent global nuclear war led to significant reductions in American and Russian-deployed nuclear forces and the abandonment of Soviet nuclear weapons and material by those nations (except for Russia) who inherited them. Today, the global strategic triangle is constituted of relatively symmetric and stable deterrence between the United States and Russia; latent deterrence between Russia and China; and asymmetric, relatively unstable deterrence between the United States and China.2
Trend 2: Regional conflicts and local security dilemmas have driven small and regional powers to proliferate nuclear weapons in recent years — most obviously between India and Pakistan, but also in Korea and potentially, in the future, Iran, offsetting Israel’s undeclared but widely acknowledged nuclear force. These arsenals are primarily targeted against neighbors who are geographically proximate rather than across continents, or against great powers that have forward-deployed forces or project power into these conflict zones. These nuclear forces are small in number and arguably serve immediate deterrent roles due to locally “hot” conflicts that could bring these smaller nuclear powers into head-on collisions.3 Consequently, nine states now wield nuclear weapons of varying levels of technological maturity — the United States, Russia, China, Britain, France, Israel, India, Pakistan, North Korea, and soon, possibly, Iran.
Trend 3: Transnational and networked terrorists and sub-national actors such as religious cults actively seek nuclear weapons capacities ranging from “dirty” radiological weapons to nuclear weapons that may leak out of state stockpiles kept by the great nuclear powers or be acquired from a small nuclear state. If these non-state actors achieve nuclear status, they are likely to use these weapons for coercive threats rather than for deterrence — or they may simply detonate them as part of their insurgent strategy against local targets (detested political elites, for example), regional targets (Israel, for instance), or global targets (the United States or its allies, Russia, and China).4
Trend 4: The revolution in military affairs has made it easier for the great nuclear powers to extend deterrence without relying on nuclear weapons of mass destruction. Forward-deployed conventional forces are still slow and bulky — but over the next two decades, they will become stealthier, smarter, faster, smaller, and, therefore, much harder to target by local conventional or nuclear weapons. Three effects of this fourth trend are already observable and will accelerate:
- Great nuclear powers, especially the United States, are likely to intervene against threatening states, especially those that seek nuclear weapons and/or lend support to non-state actors – witness Iraq;
- Small and regional nuclear powers will accelerate their development and acquisition of medium and long-range delivery systems to directly threaten the homelands of the great nuclear powers and thereby deter them from entering local frays;5 and
- Great nuclear powers, especially the United States, will invest heavily in defense-dominant strategies and technologies to counter crude, minimalist nuclear threats from third-rate nuclear powers attempting to counter local conventional dominance. Wholly new weapon systems based on converging information technology-computation, nanotechnology, and nano-biotechnology will accelerate this trend and endow the United States and other technologically powerful states with ways to partly or completely neutralize such long distance threats both to homeland security and to extended deterrence based on forward interventions.6
Considered separately, none of these trends would necessarily lead to nuclear next-use. Ordinarily, great powers will keep their distance. Local and regional nuclear-armed states will either avoid hot wars or run them as limited wars under the deterring influence of their crude nuclear weapons. All nuclear powers may keep fissile material and weapons stockpiles secure enough to avoid leakage via any route to non-state actors. Great power intervention may topple nuclear proliferating states and replace them with non-nuclear states. Small nuclear states may be unable to acquire long-range delivery systems or, if they do, be deterred from rattling their own nuclear weapons by the overwhelming offensive nuclear and conventional forces of the great nuclear powers and their local allies and friends.
Nevertheless, the complexity and unpredictability associated with the interaction of these different players at different levels is more likely than not to overwhelm controls and rational decision-making. The Cold War was managed as a nuclear balance of terror because the security elites in Washington and Moscow developed and, over time, observed some rules to the game. Nuclear weapons became the ties that bound the two adversaries in an intimate, lethal embrace. Even then, they ran close to the brink of nuclear disaster on more than one occasion. In short, these four trends converge to increase the probability that nuclear weapons will be used in war in the coming two decades.
In a four-way standoff where two local nuclear adversaries, each with backing from an external nuclear great power, may come to blows over a contested area (Kashmir, for example) with ties to global terrorism and great power interests (the Taliban and Al Qaeda, say), and in which transnational terrorists could then acquire nuclear weapons through persistent attempts to penetrate poorly secured nuclear stockpiles (in Russia, for example) and use them against one of the local nuclear powers or its backers (India, United States, or its allies), each player must become increasingly concerned about pre-emption and escalation risks to their own existence. The apocalyptic prospect contained in the core ideas of mutually assured destruction based on existential deterrence does little or nothing to avoid nuclear next-use in such complex and chaotic conflicts — especially ambiguous next-use that seeks to gain political and military advantage in the midst of fast-moving conflicts and the source of which cannot be demonstrated or is simply unknown (by ambiguous, we mean no-one claims responsibility or is easily identified as the source of the attack).
Put another way, great powers may not keep their distance if and when global stakes embroil them in regional conflicts such as that between the two Koreas. Local nuclear powers such as North Korea may collapse under pressure and lose control of their nuclear weapons in the midst of civil war and external intervention in the Peninsula. Nuclear weapons may be used pre-emptively by one faction or another in such a war to fend off further intervention or the South Korean occupation of the North. In the event of a nuclear attack on Seoul, Tokyo, Beijing, or Guam, we may never know who pulled the trigger. All this tension takes place in the midst of other transecting global issues that affect how states respond to insecurity. As the US Department of Defense put it with reference to the difficulty of US statecraft, “A series of powerful cross-cutting trends, made more complex by the ongoing economic crisis, threatens to complicate international relations… The rising demand for resources, rapid urbanization of littoral regions, the effects of climate change, the emergence of new strains of disease, and profound cultural and demographic tensions in several regions are just some of the trends whose complex interplay may spark or exacerbate future conflicts.”7
Defining the Nuclear Weapons Problem
The threat of weapons of mass destruction in Northeast Asia in the post-Cold War world is complex and multifaceted. In the conventional perspective (top-down and state-driven),8 the global threat of nuclear weapons may be disaggregated into four distinct but related problems (namely, terrorism, new nuclear armed or nuclear weapon states (NWS), existing arsenals, and regime breakdown), thereby generating roughly sixteen separate interrelated problems, as outlined in Table 5.1. On the solution-strategy side of the nuclear weapons issue, there are six obligations (no easy exit, devalue weapons, secure materials, stop transfers, resolve conflicts, deal with the now four nuclear-armed states outside of the Non-Proliferation Treaty), each of which contains multiple possible strategies for a total of twenty possible ways that regional action in East Asia could contribute to a solution of the global problem. Overall, the drivers and solutions present no less than thirty-six possible links between the global and regional dimensions of the nuclear weapons problem.
Table 5.1: Disaggregation of the Nuclear Weapons Global Problem
|
A. THREAT ASSESSMENT |
|||
|
Terrorism |
New Nuclear Weapons States |
Existing Arsenals |
Regime Breakdown |
|
1. Terrorist acquisition |
5. Nuclear Korea |
9. 1000s of weapons on hair-trigger |
13. Dual use nuclear plants |
|
2. Fissile material in Russia, Pakistan, North Korea |
6. Nuclear Iran |
10. New weapons, new tests |
14. Nuclear armed states outside Treaty on the Non-proliferation of Nuclear Weapons (NPT) problem* |
|
3. Highly enriched uranium in 40 nations |
7. Nuclear war in South Asia |
11. New threats of use |
15. End of negotiated reductions |
|
4. Nuclear black market |
8. War in Taiwan Straits |
12. Nuclear Example |
16. Collapse of NPT |
|
B. SIX OBLIGATIONS (SOLUTION-STRATEGIES) |
|||||
|
No Easy Exit from NPT |
Devalue Weapons |
Secure Materials |
Stop Transfers |
Resolve Conflicts |
Three* Nuclear Armed States Outside NPT |
|
1. No new fuel plants |
7. No new weapons, reaffirm test moratorium, ratify test ban |
11. Group to prevent nuclear terrorism, secure fissile material |
13. Implement UNSC 1540 to secure, restrict, criminalize non-state proliferation |
18. Special obligations of nuclear states |
19. Recognize 3 states will not disarm absent regional peace and global elimination but they must assume obligations |
|
2. Guaranteed fuel |
8. De-alert weapons |
12. Global cleanout to identify, secure, remove nuclear materials within four years |
14. Make Additional Protocol mandatory |
Focus on underlying causes |
20. Yes, nuclear safety, no, new reactors |
|
3. End fissile material production |
9. One-way reductions |
15. Export transparency |
|||
|
4. Punish withdrawals |
10. Plan to disarm |
16. Voluntary actions |
|||
|
5. Nuclear repossession |
17. Ground Proliferation Security Initiative in law |
A unified approach |
|||
|
6. No compliance, no trade |
Starts at the top |
||||
* This table was drafted before the DPRK became the 4th nuclear-armed state outside the NPT. Note: Items in italics are judged to be relevant to East Asia. Source: George Perkovich, Jessica T. Mathews, Joseph Cirincione, Rose Gottemoeller, and Jon B. Wolfsthal, Universal Compliance: A Strategy for Nuclear Security, Carnegie Endowment for International Peace (2007), http://www.carnegieendowment.org/files/univ_comp_rpt07_final1.pdf
On the solution side of the nuclear weapons equation, states must fulfil at least twenty disparate obligations to resolve the sixteen nuclear threats. These obligations are broken into six solution-strategies, namely, ensuring that there is no easy exit from the NPT; that nuclear weapons are devalued; that fissile materials are secured; that transfers of weapons and requisite technology, knowledge, and materiel are controlled; that conflicts are resolved; and that the special problem of extra-NPT nuclear-armed states is addressed in a way that strengthens rather than weakens the NPT system. Overall, therefore, the conventional paradigm has a complexity measure of thirty-six distinct problems and solutions, all of which are related to each other, and each of which is related in turn to other problems and solutions at various levels of the international system.
One can compare in a highly subjective manner how the global nuclear weapons problem is manifested in the Northeast Asian region by designating which elements are regional in origin or application. Of these, thirteen of the sixteen problem elements clearly originate in the region (such as the proliferation of nuclear weapons by North Korea) or are expressed in the region (such as the threats of nuclear use by the United States against the DPRK).
On the solution side of the nuclear weapons problem, roughly fifteen are solution-strategies that must either originate from states in the region (such as increasing security over nuclear materials and facilities post-Fukushima) or be applied to the region based on a global framework or the emulation of a regional or national strategy elsewhere in the world (for example, the creation of an inter-Korean fuel cycle organization like that between Argentina and Brazil).
Overall, therefore, about twenty-nine of the thirty-six facets of the global nuclear problem as viewed conventionally are to be found at play in Northeast Asia. Thus, the regional dimension of the global nuclear weapons problem is only marginally less complex (twenty-nine out of thirty-six) than the full-blown global nuclear weapons problem. Whether global or regional, the level of complexity in either case exceeds human comprehension.
Although the global nuclear weapons problem is not the same as the nuclear weapons problem in Northeast Asia, all four types of problem and all of the six obligations-solutions are at work in the region. This high degree of global-regional correspondence suggests that the underlying problems in this region may not diverge radically from those elsewhere in the world. The solutions adopted, while they must be tailored to regional realities, must also be consistent with global solution-strategies. This complexity contrasts with the formerly simple system of nuclear capacity, which commenced with a short-lived US nuclear monopoly from 1945-1949 and continued for the next four decades as a tight bipolar structure led by the United States (with its nuclear allies Britain, France, and, silently, Israel).
From Uni-polar Nuclear Power to a Bi-polar Balance of Terror
The nuclear bombs dropped on Hiroshima and Nagasaki in 1945 marked the zenith of American power in the 20th century. In the next half-decade, the former Soviet Union tried to catch up and as the Cold War began, the United States viewed nuclear weapons as extraordinarily powerful weapons of war, not of deterrence and peace.
The Korean War was the first major conflict in which nuclear weapons played a political-symbolic as well as a military role. Not only did US presidents attempt to compel Chinese leaders to abandon their intervention in the Korean War and to negotiate an end to hostilities on terms advantageous to the United States, but also the shadow of nuclear threat was cast over Korea itself and affected the conduct of the war by the military. For example, in the Korean War, US navy ships were distributed rather than left concentrated in Korean ports and vulnerable to nuclear attack. However, Korea was primarily a protracted conventional conflict based on attrition, maneuver, and air superiority. Nuclear weapons barely affected political or military outcomes although the War did serve as a laboratory for American strategic practitioners to explore how the nuclear threat worked in psychological terms against Chinese and North Korean personnel. Thus, the Korean War prefigured the role of nuclear weapons, but it did not yet reflect the operation of the nuclear threat in a pronounced manner.
In the aftermath of the Korean War (and in response to the demobilization of US forces), the United States substituted nuclear weapons for conventional forces and positioned itself to retaliate massively against the former Soviet Union and China. This was also the moment in which the United States laid down the strategic architecture that combined the ideology of nuclear deterrence with the institutional framework of integrated forces and joint organizations to support combined nuclear and conventional forces, based on unique American nuclear weapons capabilities — including the full spectrum of warheads, delivery systems, bases, command-and-control, and communications-and-intelligence systems needed to fight a nuclear war.
Starting in the mid-1950s in Japan and in 1958 in Korea, US nuclear weapons were forward-deployed to land bases as well as carried aboard US naval forces. By now, the former Soviet Union had tested and deployed its own nuclear weapons, and US strategic thinkers were starting to develop rationales for nuclear forces that recognized their uniquely destructive nature — so much so that they were repulsed from forward-deployment in post-war occupied Japan by a popular movement that led to the removal of land-based weapons from Japan itself in 1960 (but left unrestrained the transit by air and sea of US nuclear weapons in a secret understanding that came to light only in 2010, although it was known to exist for many decades beforehand).
Although China had not yet developed, tested, or deployed its own nuclear weapons, US nuclear forces routinely targeted the former Soviet Union and China as one bloc in the US nuclear war plans maintained at the headquarters of the regional Commander-in-Chief in Hawaii. By now, the United States had created a set of bilateral alliances across the Pacific, and the Cold War was fully underway. The two blocs came closest to direct military confrontation in the 1958 Taiwan Straits Crisis, in which the United States positioned nuclear forces in Taiwan to deter any expansion of the Chinese efforts to occupy Nationalist-controlled islands, thereby risking the use of nuclear weapons against China should Beijing have decided to escalate. This was the first instance in which American strategists began to comprehend fully the risks being run by over-reliance on nuclear weapons to substitute for conventional force.
The escalating Vietnam War was the next theater in which nuclear weapons played a role. Again, due to the primarily counterinsurgent nature of the war, and overwhelming American control of the air war, the United States could not find a way to bring the enormous firepower of nuclear weapons to bear on the ground — although the option was studied carefully in the Pentagon.9 However, it is possible that the Southeast Asia Treaty Organization (established by the United States with its local allies to prosecute the Vietnam War) played a role in deterring Chinese direct intervention in the war due to the image it projected of being ready and able to fight nuclear war — an option regularly exercised by US forces operating in the region with allied navies.
Tri-polar Nuclear Deterrence
Although the United States (plus Britain and France) and the former Soviet Union fielded the vast majority of nuclear weapons at home, on ships, or on land (the former Soviet Union did not deploy nuclear weapons on allied territory, only on its ships in the Indian and Pacific Oceans), China joined the nuclear club in 1964, launched its first missile in 1966, and tested its first fusion bomb in 1967. With subsequent bomber and long-range missile deployments in the early 1970s, the bipolar balance of terror became a triangle of nuclear threat. This included a 1968 artillery shootout between the former Soviet Union and China at a time when the United States targeted both with nuclear weapons, but tilted towards China as Nixon made his famous move to meet with Mao in 1972, a central aspect of his global redesign of world power.
The trend of integrating nuclear and conventional forces as complements for war-fighting rather than as substitutes for deterrence accelerated in the 1970s to the point where US military emphasized to their own troops and to allies that no distinction could be made between the two types of forces — they were dual use. The ferocity of the Cold War in the 1980s led to an escalation of risk-taking in the region in two cases, both of which came perilously close to direct combat between the United States and the other two nuclear states in the region.
The first was a series of incidents in Korea that stretched back to the late 1960s, during which North Korea conducted provocative covert conventional attacks on South Korean territory or abroad (in Rangoon, for example, when it attempted to assassinate the majority of the ROK Cabinet). This series of attacks culminated in the August 1976 confrontation over a poplar tree in the Demilitarized Zone during which forces on both sides mobilized for full-scale war. On August 18, 1976, the US military decided to remove a poplar tree in the Joint Security Area in the Demilitarized Zone that was blocking the northward view.10 As a team of US and ROK soldiers began to cut the tree, they were attacked by North Korean soldiers. In the melee, two Americans were killed, bludgeoned by axe handles. On August 21, US and South Korean forces mounted Operation Paul Bunyan, backed by mobilized forces across the entire Peninsula, including the movement forward of tactical nuclear weapons.11 The then-US Commander in Korea, General Richard Stillwell, had pre-delegated authority to use artillery to bombard a barracks north of the DMZ should the DPRK respond to the task force. In fact, not long after the tree was cut down, the North Koreans fired on a US helicopter flying over the DMZ and hit it — a casus belli if Stillwell had chosen to act on it. Luckily, he did not. For the next month, the United States sent flights of B52 bombers up the Korean Peninsula, veering off at the last moment. Henry Kissinger noted at the time that this huge show of force was to “overawe” the North Koreans.12 “I have never seen the North Koreans so scared,” Kissinger commented on August 26, 1976.13
The second case was the prospect of a naval-nuclear shootout between American and Soviet naval-nuclear forces in the North Pacific or one of the coastal seas close to the former Soviet Union. The peak of this risk may have been after the former Soviet Union’s air defenses shot down the South Korean airliner KAL 007 in 1983, leading to naval collisions in the area where debris splashed into the ocean. Elsewhere, Soviet submarines engaged in a cat-and-mouse game with American adversaries. The risk was more that the forces themselves would go awry and inadvertently start a nuclear war rather than that some strategic interest would bring American forces to blows with Soviet forces, leading to nuclear war.
At the same time, American allies including Australia, Taiwan, South Korea, and even Japan began to explore directly and indirectly the acquisition of independent nuclear forces due to their fear that the American extension of nuclear and conventional deterrence was of deteriorating credibility and utility after US forces had been driven out of Vietnam in abject defeat. Of these efforts, South Korea did most at the time when unilateral conventional and nuclear withdrawal was imminent. But they did not go far down the proliferation pathway due to American pressure in each of the four decades since, even during periods when they toyed with the idea of developing and deploying their own nuclear or chemical weapons. Japanese explorations concluded that proliferation was a bad idea because it was unlikely to create a strong deterrent force in a short time, and that it would come at a high political, economic, and military cost. Taiwan capitulated quickly to pressure from the United States that exposed its dependency on US military aid and direct support against the threat of mainland attack. Thus, this period demonstrated the resilience of American nuclear hegemony, but also revealed the powerful stress that was starting to affect the political-ideological basis of allied consent to American nuclear leadership in the region.
Nonetheless, until the late 1980s, American nuclear hegemony ruled supreme. The popular overthrow of the South Korean military dictatorship in 1987 was in part due to the subordination of local military forces to American nuclear forces aimed at the Soviet Union, and this bottom-up rebellion directly collided with the deployments that undergirded nuclear hegemony. Another key factor in declining hegemony was the region-wide Nuclear Free and Independent Pacific Movement that coordinated anti-nuclear warship and basing protests, which led to the abdication from the nuclear alliance of New Zealand — the mouse that roared when it banned nuclear ship visits by its putative American ally.
In an adroit move to defuse this opposition and respond to the dissolution of the former Soviet Union, then-President George H. W. Bush ordered the removal of all theater and tactical nuclear weapons in the region from bases and surface warships — a task completed in 1992. This adjustment recognized the limits of American hegemonic power to attend to the most urgent security tasks in the region, including the rapidly emerging threat of a North Korean nuclear weapons program. It also reflected the judgment that American and allied conventional forces were able to fulfill almost all the war-fighting missions formerly attributed to crude nuclear weapons, a judgment justified by the increase in range, precision, and lethality demonstrated during the Gulf War with Iraq in 1990-91. Moreover, conservative strategists were disenchanted with the passive notion of deterrence based on mutually assured destruction. They were anxious to test and deploy missile defenses to increase the ability of the United States to achieve its own security with or without allied support, and without regard to the intentions and capacities of other nuclear-armed adversaries — at this stage, Russia and China.
Things Fly Apart
After popular opposition pushed nuclear weapons out of public view in Japan in 1960, states became almost completely predominant in deciding how nuclear weapons affected security in the region. Anti-nuclear sentiment pushed nuclear weapons out of Okinawa in 1972, and the democratic uprising in South Korea in 1987 laid the foundations for the removal of nuclear weapons in 1991. With offshore nuclear submarines, home-based long-range missiles, and long-range bombers, the United States and the former Soviet Union deployed enormous numbers of nuclear weapons to strike fear into the minds of adversary leaders and the hearts of their populations. China deployed nuclear weapons to keep the two superpowers from coercing it. Two small powers — Taiwan and South Korea — attempted to get out from under the American thumb by developing their own nuclear forces, but were stopped almost immediately by the United States.
When the Cold War ended abruptly and the former Soviet Union dissolved, the region flew apart and fractured in many different directions. The relatively simple bipolar and even the more complicated tri-polar balance of state-based nuclear forces became far more complex — not just in the quantitative sense that the number of states began to increase, making it difficult to live, in Albert Wohlstetter’s memorable phrase, in a “nuclear-armed crowd.” But also in the qualitative sense that many different types of states and social entities, including non-state actors, became influential agents of change. The dynamics were embedded in a global set of processes and networks that linked the local, regional, and global aspects of the nuclear weapons problem and solution in a way that quickly surpassed the management capacity of the United States as nuclear hegemon.
Unsurprisingly, North Korea emerged as the most serious contender in the region for state-based nuclear proliferation when, in early 1992, the International Atomic Energy Agency (IAEA) declared the North’s declaration did not include plutonium known to have been reprocessed at Yongbyon. The DPRK’s nuclear aspirations had been apparent for many years. Alarm bells began to ring over its nuclear program in the early 1980s, leading the United States to enlist the former Soviet Union to induce the DPRK to join the NPT and to allow IAEA safeguards to come into force over its declared nuclear facilities. North Korea’s breakout not only tore a hole in the fabric of the NPT, it threatened the foundations of US nuclear hegemony: its legitimating deterrence ideology, institutional integration with allies, and uniquely powerful nuclear forces. It also introduced a new element, in that it primarily used its nuclear threat for compellence purposes, whereas the other nuclear weapons states had reserved their nuclear threat for deterrence (except for the United States on a few, failing occasions). Nonetheless, North Korea was still a state playing a nuclear deterrence-compellence game that other states had played for decades in one way or another; while its trajectory was an unnerving departure from past state practice, it was a latecomer that reinforced the role of nuclear weapons in international relations between states and thereby reaffirmed the status quo.
In contrast to North Korea’s entirely predictable nuclear proliferation, a relatively serious attempt by a non-state actor to develop nuclear weapons in the region was completely unanticipated. This development originated in Japan in the form of a murderous, apocalyptic religious cult, the Aum Shinrikyo. At one point, they had assets of more than a billion dollars and scientists in laboratories developing chemical and biological weapons, some of which they tested in Australia on sheep in 1991. They had attempted to buy a nuclear weapon in Russia before attacking a subway system in Matsumoto City with sarin nerve gas in 1994, followed by a second attack on the Tokyo subway system in 1995.
Aum Sinrikyo prefigured the rise of mega-terrorism that culminated in the September 11, 2001 attack on New York City by Islamic fundamentalists operating in networked cells. Thus, in the few years between the collapse of the former Soviet Union and the rise of Aum Shinrikyo, the nuclear weapons problem shifted radically from being merely complicated to becoming one of enormous complexity.
Complexity-based Definition of the Nuclear Weapons Problem
In contrast to the conventional paradigm of the nuclear weapons problem delineated above, here we will attempt to define the true complexity that characterizes the nuclear weapons problem in Northeast Asia in the 21st century. To do this, we will examine the nuclear weapons problem anew using the attributes of simple systems versus complex systems, as outlined in chapter 2. In sum, a complex system has many agents, many interactions between these agents, decentralized decision-making by these agents, is irreducible, is open to flows across borders with other systems, is dynamic, tends towards entropy, has many positive and negative feedback loops, and generates surprising outcomes.
As we noted above, humanity survived half a decade of uni-polar American nuclear power; a decade and a half of a perilously simple, bipolar US-Soviet balance-of-terror system; and three and a half decades of a tri-polar US-China-former Soviet Union nuclear triangle. Even then, the strategic calculations entailed by a nuclear “truel” were mind-boggling.
As Paul Bracken explains, “truels” — or three-way standoffs — are inherently more unstable than duels due to the inability of each party to know if the third is holding fire in the hope of the other two eliminating each other. He notes that in a three-way “‘truel’, in which each of three competitors is in direct opposition against the other two…The players have to decide (l) whether to shoot at all, and (2) if so, which countries to shoot at, with how many missiles, at what targets, and in what order.” Moreover, “solutions to the problem require more stringent assumptions about communication, trust, and commitment than with two players, where only weak assumptions are needed to achieve crisis stability. The number of possible scenarios is enormous compared to the two-person duel.” Part of the problem with the emerging global triangle at the end of the Cold War was precisely that no one knew if China recognized or played by the same rules.14 This led to some weird policy options. At one point, for example, the United States considered conducting a nuclear strike on Soviet forces in Asia, weakening them so that China could occupy central and Far Eastern Soviet territory.15
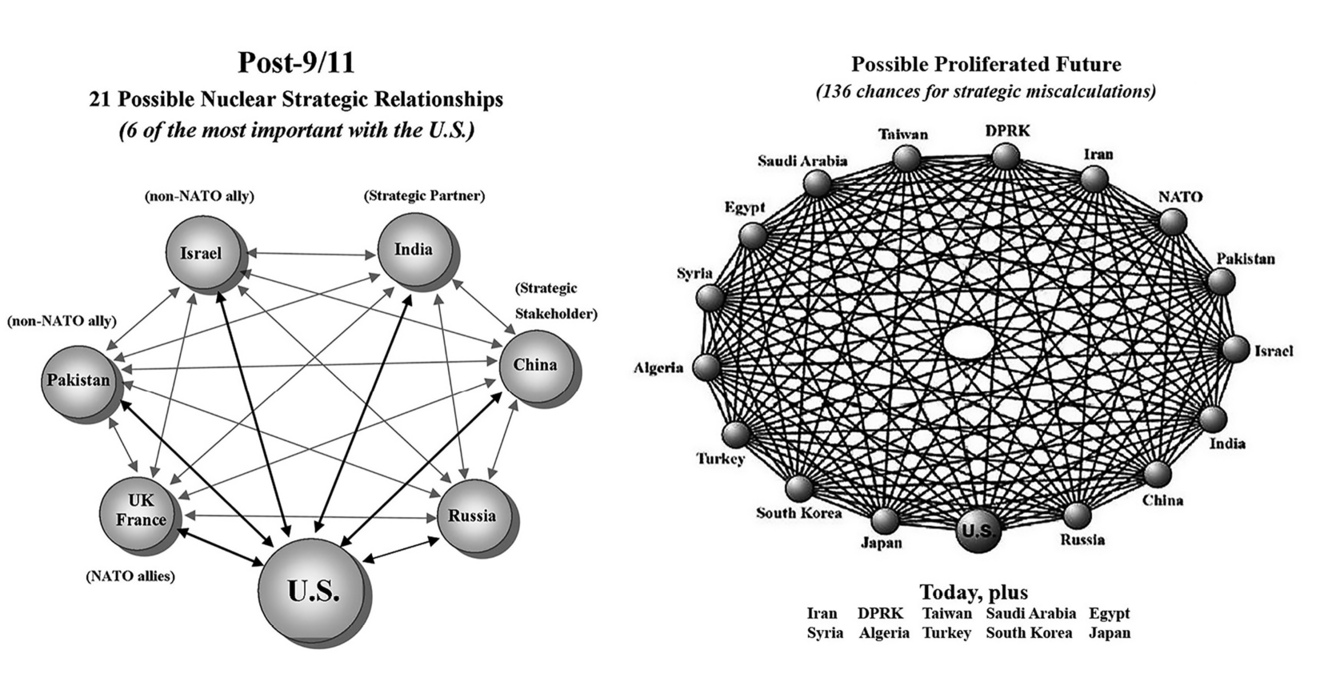
Now, we face a future in which no fewer than nine nuclear-armed states co-exist. Still, a relatively manageable level of complicated, multi-polar nuclear threat involving 21 possible relationships (or 42 one-way links) is shown in Figure 5.1 — but this is embedded in a fluid set of alignments and coalitions over novel issues and problems such as huge tsunamis, global pandemics, regional conflicts, economic crisis, and uncontrollable climate change. when North Korea is added the mix, its nuclear breakout further complicates relationship management, so that now 28 relationships or 56 links must be constantly monitored.
Figure 5.1: Phase Transition from Complicated to Complex Nuclear Weapons Problems
Source: Henry Sokolski, “Nuclear Abolition and the Next Arms Race,” in In the Eyes of the Experts: Analysis and Comments on America’s Strategic Posture, Selected Contributions by the Experts of the Congressional Commission on the Strategic Posture of the United States, ed. by Taylor Bolz (United States Institute of Peace Press, Washington DC), pp. 207-08, http://www.usip.org/files/In the Eyes of the Experts full.pdf
This complexity looks ready to increase exponentially in less than a decade should the existing nuclear states be joined by an additional eleven nuclear-armed states in Northeast Asia, the Middle East, and North Africa: the state of affairs will move from 21 to 136 relationships and from 42 to no fewer than 272 one-way links.
In the first nuclear era (1945-1990), the state-based nuclear threat system exhibited a strong degree of central control by the United States with respect to the nuclear decisions of its allies. Even those countries that were nominally independent, such as France, eventually aligned with NATO — and the system was able to directly block and redirect a number of proliferating states.
Thus, in the conventional paradigm, two of the most critical characteristics of the second, post-1990 nuclear era are, firstly, that a number of states — most importantly, North Korea — have proliferated in direct opposition to the great powers, including those represented on the UN Security Council; and secondly, the Kahn non-state network has emerged and proved capable of evading Western intelligence for decades while trading in material, technology, and knowledge essential for the development, deployment and use of nuclear weapons — thereby demonstrating that non-state actors are nuclear weapons-capable.
The combination of exponentially increasing inter-state nuclear threat relationships that must be managed with adversarial states such as North Korea and Iran breaking out of the Cold War control system reconstitutes the nature of the nuclear weapons problem, both globally and regionally. However, the qualitative transformation of the international system arises not merely from the addition of more nuclear-armed states per se, but from other powerful trends. These include the following: accelerating functional integration, especially economic, within the region and especially between China and the other major economies in Northeast Asia; the simultaneous convergence and diffusion of information and of nano- and bio-technology that may result in new types of weapons of mass destruction alongside nuclear, chemical, and biological weapons; generational change in the established nuclear weapons and nuclear-armed states, meaning that historical lessons may be lost and have to be relearned at great risk; and the increasing probability that a non-state actor will obtain access to nuclear weapons and either take a state hostage or use a nuclear weapon against a state. The latter risk is closely related to the rise of global crime networks on the one hand, and global terrorist networks on the other. They converge in locales with weak or no governance, and the general globalization of trade and mobility of people results in the increased porosity of society to bottom-up, networked nuclear weapons strategies.
These modern attributes of the nuclear weapons problem in a new, more diverse, and turbulent context make it a truly complex problem and no longer amenable to central control. There are now many autonomous state-based decision-making centers, each capable of starting a nuclear war and each susceptible to errors of information, misinterpretation, misjudgment, biased interpretation, and degradation of decision making at times of stress. Interacting with these states across levels and borders are numerous non-state entities, at once political-ideological in the orthodox sense of insurgencies aimed at overthrowing and supplanting specific governments, but also motivated by a range of core goals including religious, cultural, and other values that are not amenable to deterrence. Not least of these problems is the fact that many non-state actors “have no fixed address” and may welcome rather than fear capture or death, being thereby largely immune to deterrence in the standard military frame of reference.16
Increased Risk of Nuclear Next-Use
In the Cold War, the main risk of nuclear war in the region emanated from a global nuclear war that would begin in Europe (or the Middle East) and escalate to the Asia-Pacific region; in a naval-nuclear Soviet-American shootout in the North Pacific that would escalate to a regional or global nuclear war; or in a war in Korea that would escalate to nuclear war on the doorstep of China and the Soviet Union — either of which might have become involved.
Today, the risk of nuclear next-use is far more diffuse and unpredictable. There seems to be no reason to anticipate a global nuclear war between the United States and Russia, let alone a war pitting either of these nuclear weapons states against China. A nuclear war between North Korea and the United States and its allies is conceivable and could escalate to involve China. A naval-nuclear shootout in the Taiwan Straits between the United States and China is also conceivable given the stakes, the structure of the situation, and the forces involved. The situation could become even more complex should all states in the region become nuclear-armed, as was suggested at one point during the Cold War as a possible and (some argued) even desirable state of affairs.
Nuclear terrorism in the form of an attack on a spent fuel pond, reprocessing center, or nuclear reactor, or through the acquisition and threat of deployment and/or use of a nuclear weapon, especially a nuclear weapon, is conceivable. A nuclear terrorist attack would likely be against a port city (but any city could be held hostage or attacked). Such an attack might not be attributed to a specific aggressor, or its point of origination might be ambiguous, leaving everyone guessing as to what comes next. This section examines this spectrum of possible nuclear next-use situations, and concludes that after declining in the aftermath of the end of the Cold war, the cumulative risk of another nuclear attack is again on the rise.
Nuclear Next-Use in Korea
To anyone conversant with the Korean Peninsula, the simplistic realist notion that states strive constantly for stability and dominance at the same time, thereby generating instability, sounds all too familiar.
Viewed from the perspective of complexity theory, states as the international system’s highest level or meta-agents are indeed independent, as are many of their constituent elements; even in North Korea, some players have a degree of autonomy. No one controls how events unfold in and around Korea because there are too many driving forces involved at the same time for the system to behave predictably. The interstate system in Northeast Asia is composed of states of very different sizes, political cultures, and power capacities, creating asymmetric relationships that are themselves difficult to understand.
In this complex terrain, market and civil society non-state actors are active both domestically and transnationally and can, without warning, ignite change or induce states to shift their strategic direction by a few degrees. In situations as super-charged with restrained force as the Korean Demilitarized Zone, simple incidents involving the actions of only a few people can bring the conflict system close to a shooting war in only a few seconds. In May 2010, for example, hungry North Korean soldiers desperate to find food entered the Demilitarized Zone to go fishing, leading to a shootout with South Korean soldiers.17 In 2011, marines on a small ROK-controlled island fired upon a South Korean commercial airliner thinking it was a North Korean jet attacking the South. In North Korea itself, the slow, incremental, but inexorable degradation of the electricity transmission and distribution substations has gone so far that a long cold period could shut down many substations forever — no matter what is done by North Korean technicians to improvise solutions. Such an event could lead to a massive humanitarian crisis in the midst of winter to which South Korea and its partners have no solution — indeed, they are not even aware of the existence of this crack rising to the surface of North Korean “stability.” These are examples of small changes at one scale of the system which can affect another scale of a problem rapidly, unpredictably, and structurally — a moment sometimes called a “tipping point.”
Exactly how would a nuclear war unfold in Korea? No one knows. But we do know the US Strategic Command (STRATCOM) maintains a database of possible nuclear targets in North Korea that includes wide-area attacks on ground forces massing to attack South Korea, key command and control sites that would be attacked to “decapitate” North Korea’s leadership, and many other military and logistical sites all over North Korea. Warheads could be delivered to these targets by strategic bombers flying all the way from the United States and back, by land-based intercontinental missiles, or by submarine-launched missiles from the Pacific Ocean. STRATCOM would send Nuclear Employment Augmentation Teams or teams of nuclear-targeting specialists to US Forces Korea to advise the local commanders on nuclear targets. The locals would likely find many of these options useless due to lack of local knowledge and would end up improvising selection of targets and target coordinates for nuclear weapons against North Korean sites or mobile units in the midst of a war, under immense stress.18 For its part, the DPRK has a small number of warheads, probably fewer than ten, and in our assessment, these would be used near the DMZ in either a pre-emptive or retaliatory attack to create craters in the corridors through which US-ROK ground forces might otherwise attempt to pass. Our best guess is that for all the hubbub over its long range missile tests (four out of five failed) and nuclear tests (one out of three failed), the DPRK has no reliable way to deliver its warheads outside its own territory.19
There are still a number of pathways by which a war in Korea could escalate to nuclear war. Bruce Bennett at RAND has imagined a number of such cases.20 One is that for whatever reason, likely inadvertently, a major artillery exchange occurs north of Seoul along the DMZ. This escalates into an attack on northern Seoul by the DPRK in an attempt to stun the ROK into halting a push to move the DMZ northwards to reduce Seoul’s vulnerability to future artillery and rocket attacks. Bennett suggests the move would induce the DPRK to switch to chemical weapons to reverse the tide. Such an attack, depending on targeting, wind, and the agent used, could lead to immense civilian casualties, which could then lead to pressure on the United States to reply with nuclear weapons to deter further escalation by the DPRK or to eliminate its chemical weapons capacities. Such a spiral is all too easy to envision and, historically in other conflicts, has proved very hard to halt once under way.
Factors that might deflect or shape American nuclear attacks in a renewed war with Korea (other than wind and weather, which could lead to an unacceptable radiological threat to US and ROK forces as well as to civilian populations whether north or south of the DMZ) include the “balance of blame” as to who started the war, the question of whether China enters the war, and what other regional and global contingencies would already pre-occupy American leaders or interact with a war in Korea. The latter could include tension and/or war in the Taiwan Straits, a Middle Eastern crisis involving Iran, instability in China itself, and the speed and type of South Korean response to North Korean provocation (which could become extremely bloody should it entail rapid occupation of North Korea to suppress a civil war after the collapse of the North Korean regime). In such a context, deterrence is unlikely to be a straightforward exercise in communication of threat, as conceived during the Cold War. Instead, the situation would be more like an arena full of bucking broncos, with each rider cracking whips to try to control the other riders and scare their horses, creating chaos and mayhem.
Nuclear Next-Use between Nuclear Weapons States in East Asia
Nuclear war in Korea would be bad enough, but it would likely remain confined to North Korea. Of even greater consequence would be a confrontation between China and the United States over Taiwan, should Taipei declare independence from the mainland. If such a thing occurred, then China has declared that it would have no option but to attack and occupy Taiwan. Moreover, some Chinese security officials have let slip that its no-first-use declaration (with regard to the use of nuclear weapons) applies only to external conflicts — and because it regards Taiwan as an integral part of China, no-first-use does not apply to it. One may conclude that China would not use nuclear weapons against Taiwanese forces attempting to stop a cross-straits, air-sea attack by China. But it is far from clear whether China would feel restrained against first-use of nuclear weapons against US aircraft carrier groups that would otherwise operate beyond striking range of most of China’s air and naval forces — thereby bringing China’s nuclear-tipped intermediate range missiles into the equation. Also ambiguous is whether nuclear missiles might be fired at US forward bases on American and allied territory in the region if they were used to support a conventional naval and aerial defense of Taiwan against Chinese attack, thereby linking the fate of the allies to America’s extended deterrence of attacks on Taiwan, both conventional and nuclear. Because China has the assured capacity to fire nuclear weapons at these allies, whereas North Korea does not, the Taiwan Straits issue is far more significant in terms of the risk of nuclear attack on Japan than is North Korea. For South Korea, however, the North Korean military and nuclear threat to the South is far greater than that arising from China via a conflict with the United States over Taiwan — not least because US forces in South Korea have little direct bearing on the United States’ ability to prosecute such a war (and therefore, China would have little military reason to waste warheads on South Korea).
Currently, it is clear that from a military viewpoint the United States has absolute and relative superiority, including “escalation dominance,” which in almost every respect would block a Chinese attack on Taiwan — even without Taiwanese forces playing a role.21 But the balance of military forces is not the only determinant of the robustness of deterrence. The balance-of-will, based on relative interest in the independence of Taiwan, is clearly tilted in China’s favor, whereas the interest of the United States lies primarily in its reputation as a reliable ally able to stand up to rising Chinese power in the region. Of course, Taiwan is not an ally of the United States, but the impact on other allies such as South Korea or Japan of allowing China to militarily occupy Taiwan and reverse its secession from China would be to shatter the credibility of the United States as a security patron. It could also set in motion proliferation dynamics among US allies and motivate North Korea to use conventional force to put pressure on South Korea to evict US forces.
Due to the centrality of Taiwan’s decision on whether to slowly reunify with China or declare independence, the United States plays a role in this conflict zone as a “pivotal” deterrent. On the one hand, it reassures China that it will restrain such a move by Taiwan’s leaders, which requires that it demonstrate the military capacity able to defend credibly against Chinese attack, with all the attendant risks of escalation, including nuclear escalation. On the other, the United States deploys forces in the region to deter China from attacking, thereby reassuring Taiwan and underlining the point that a declaration of independence would be a needless provocation that risks degrading US protection against China.
Unfortunately, it is not as if these two scenarios — war and nuclear war in Korea, and war and nuclear war in the Taiwan Straits, China, and the wider region—exist in separate worlds. In the real world, the decisions of Taiwanese and North Korean leaders will be made in the midst of crises with an eye to how the other’s possible conflict affects their respective great power’s adversaries and abilities to respond. A war in Korea would so entangle China and the United States that the Taiwanese might think that they could declare independence in the belief that China would be unable to fight on two fronts at once, thereby achieving a fait accompli.
Conversely, in a war over Taiwan, North Korea could decide to move decisively while a window of opportunity remains open; meanwhile, the ability of the United States to reinforce its troops in Korea would be constrained by mobilization to support Taiwan.
Moreover, even in times of routine insecurity, North Korea and Taiwan have potential joint interests that could come into play. In 1997, Taiwan’s power company contracted with North Korea to store nuclear waste.22 Taiwan had previously attempted to build its own bomb in the 1980s and has an advanced nuclear fuel cycle capacity to support its nuclear power program. Taiwan is also a “black hole” in terms of non-state-based trading in dual-use and nuclear-specific commodities needed for a nuclear weapons program, and it has been the transshipment point for a number of such transactions between Japanese firms and North Korea. If these two international outcasts found themselves isolated and highly insecure — especially in the case of Taiwan — it is possible that North Korea could assist Taiwan to gain its own nuclear weapons capability in return for hard currency, technology, and even informal alignment with regard to how to play hard ball with China and the United States in a concerted manner. As Dingli Shen put it, “Even if China would not ask for it, a nuclear North Korea’s ability to pin down US forces in a Taiwan Strait contingency deters America’s consideration of possible military intervention.”23
Thus, the Taiwan factor overlays all other considerations for China and the United States, and it also affects the calculus of US allies and North Korea in all their bilateral relationships. Nuclear risk in Korea is linked directly and indirectly to nuclear risk in Taiwan. Although both can be resolved separately, the two ongoing regional conflicts must be managed jointly — and adroitly — by the United States and its allies, and by China, if war and nuclear war are to be avoided. Moreover, the reverse is also true. If the Taiwanese situation is resolved peacefully and reunification is achieved without the use of military force, then North Korea’s geo-strategic significance for China would be greatly diminished, and the conflict in Korea would likely become much easier to resolve as well.
Nuclear Next-Use in a Nuclear-Armed East Asia?
In 1982, John On-Fat Wong wrote a bleak dissertation at the University of Wisconsin positing that every state in Northeast Asia had gone nuclear, leaping from three nuclear weapons states (United States, Russia, and China) to seven (the additional countries being North and South Korea, Japan, and Taiwan).24 In this imagined world, superpower conflict continued, local conflicts drove local proliferation, leaderships changed explosively, and regimes disintegrated.
Wong examined four geopolitical scenarios (1990) for Northeast Asia (he included Taiwan). These were: general détente, limited bilateral détente, a new cold war, and a general cold war. Next, he listed strategic targets for nuclear weapons in each country, basically cities and industrial areas, and then determined the firing point from which a nuclear weapon attacking each of these targets would be launched. From this, given blast effects and other means of degradation such as warhead fratricide, he derived the warhead yields and delivery systems required to achieve varying levels of desired annihilation. These targets were “countervalue” in nature rather than “counterforce” in Wong’s approach. He wanted to determine what a generalized nuclear-veto system of multilateral nuclear deterrence would look like if McNamara’s notion of Mutual Assured Destruction were applied to each target country in the search for stable deterrence. Then, he set out to rejig the nuclear postures required to conform to the local requirements for strategic deterrence given the size of each state and its insecurities as defined in each of the four scenarios.25
Wong’s regional nuclear nightmare vision is worth revisiting today because we now have four nuclear-armed states and only two non-nuclear states in the region, and the trend is moving toward his imagined world of full proliferation.
Wong began by determining that lesser versions of mutual assured destruction were feasible between small and middle powers armed with nuclear weapons. Even without secure assured retaliatory forces on the American model of a three-service strategic triad, these powers could still wreak “assured heavy damage” on each other (though not the 70 or 80 percent damage demanded by McNamara’s best and brightest as sufficiently “deterring” during the Cold War). Of course, the great powers armed with thousands of warheads could still exterminate the medium powers, so the reliability of the medium power arsenals to deter great power pre-emptive attack is inherently low. The inevitable lack of a secure retaliatory capacity on the part of small states suggests that a generalized nuclear veto-system based on universal proliferation in Northeast Asia would be prone to pre-emptive strike in the search of some states for damage limitation.26
Wong noted that small nuclear powers — like North Korea — are more of a nuisance than a threat to the status quo of the nuclear threat system between the great powers. The existence of a number of middle power, nuclear-armed states such as Japan or South Korea could affect the force ratios between the great power, nuclear-armed states. Moreover, the small nuclear power is vulnerable to pre-emption at any time, whereas the middle power is much less so, although it could not hope to conduct a pre-emptive strike against a great power nuclear state and hope to survive, at least not for very long.
Wong pointed out that the relationship between two small nuclear-armed states — if both Koreas gained nuclear weapons, for example — would be one of mutual vulnerability, as neither would have a secure nuclear retaliatory force and both would have relatively concentrated and easily targeted industry and populations.27 In a region composed of great, middle, and small powers like Northeast Asia, only the great powers can wreak mutually assured destruction on each other (in fact, only Russia and the United States could do that then or today to each other). The great powers could also inflict assured destruction on middle and small powers, and middle powers in turn could inflict assured destruction on small powers.
Moving along the other direction in scale, small powers and middle powers could assuredly heavily damage each other, but not the great powers. And all the powers could massively retaliate against each other (for example, by destroying one or two cities, equivalent to “ripping off an arm” as the Gaullists used to say of the French nuclear force de frappe) against any power, small, middle, or large. Summarized in Table 5.2, these distinctions capture some of the effects that Wong anticipated could arise from universal nuclear proliferation in the region.28
Table 5.2: Probable Doctrinal Preferences
|
Deterrer |
Deterree |
||
|
Superpower |
Medium Power |
Small Power |
|
|
Superpower |
AD |
AD |
AD |
|
Medium Power |
AR |
ARD |
AD |
|
Small Power |
AR |
AR |
MD/PD |
|
AD Assured Destruction AHD Assured Heavy Destruction |
|||
Source: John On-Fat Wong, Security Requirements in Northeast Asia (PhD dissertation, University of Wisconsin, 1982), p. 77.
It is worth quoting Wong at length to highlight the implications for “stability” in conflicts between middle and small powers if nuclear hawks in each country of the region have their way:
Given the vulnerability of the small power and its nuclear forces, enemy destruction is more “probable” than “assured.” This condition of pre-emptive instability suggests that among the small powers, “mutual vulnerability” or “mutual probable destruction” is a much more appropriate description of their strategic relationship than “mutual assured destruction.” Once they have acquired some quantity of nuclear weapons, the condition of “mutual vulnerability” has been created. It is possible to imagine asymmetry of doctrines among small nuclear powers (e.g. one pursuing assured destruction while the other superiority). However, the differences in their nuclear arsenals will not alter their vulnerability. This is not surprising since (1) regardless of their doctrinal preference, there are real limits to their nuclear arsenals, and (2) the effectiveness of pre-emption by conventional means is enhanced by relatively small and dense target structures and geographical proximity.29
The significance of this situation is immediate in Korea today. As Wong explained:
[T]he paucity of means usually forces the small power to adopt a relatively rigid strategic posture and force structure vis-à-vis the large power. This rigidity of posture has a paradoxical effect on the credibility of the small power nuclear deterrent and the stability of the nuclear deterrence system. In a sense, the enhancement of the small power deterrent contributes to the greater overall stability of the deterrence system. However, due to the severe limitations on its capabilities, the real choice of the smaller power in time of crisis is between strategic surrender and suicidal war. There is a built-in instability in this type of situation. Overall crisis stability has been eroded, in fact, by the possession of nuclear weapons by small powers.30
Wong calculated that for one country (in this case, South Korea) to achieve a second strike capability against the other six countries in his most insecure scenario for 1990 (a revived Cold War), it would have taken 820 one-megaton warheads capable of being fired against 600 cities with over 300 million people — an enormous and incredible arsenal for a small power like South Korea.31
More realistically, he noted, to bomb North Korea into the stone age would have taken “only” seventy-five 200-kiloton weapons, buttressed by ten more one-megaton warheads aimed at China, Russia, and Japan (which was assumed in his scenarios to also have become a nuclear weapons state) to deter them from entering a war with the North.32
We dwell on Wong’s extremist heuristic to highlight the threat that past, present (North Korean), and any further proliferation poses to national and human security in Northeast Asia. The risk of nuclear next-use in such a world would increase dramatically and likely in non-linear ways, giving rise to what Wong called “probable assured destruction” — although he reserved this term for the likely fate of small nuclear-armed states in his scenarios.
We have referred in previous sections to how American, Korean, and Chinese nuclear weapons could lead to nuclear next-use. Here, we should note that Russia also maintains nuclear forces and some may still be deployed in the Russian Far East, remaining salient to Chinese and American strategic forces and to Russia’s relationships with the three small powers in the region, that is, North and South Korea and Japan. Russia’s Far Eastern provinces are militarily weak and isolated from European Russia. Russia has re-emphasized the role of tactical and theater nuclear weapons in its nuclear doctrine, relying on the concept of early-use to stun conventional attack.33 Facing rapid Chinese military modernization, Russia may reassert the enduring nature of its nuclear forces in this region, thereby contributing — yet again — to the vulnerability of its neighbors in the region, especially of Japan and South Korea.
Nuclear Next-Use and Nuclear Terrorism
The proliferation, acquisition, deployment, and use of weapons of mass destruction, especially nuclear weapons, are no longer the sole province of states. Globally-networked insurgencies and ideologically-motivated terrorist organizations, have begun to converge34 with global criminal organizations that traffic in people35 and contraband,36 and in many countries are allied to powerful political figures, sometimes providing private militia to them.37 Conditions of global trade, finance, and investment make borders increasingly porous to these flows and portend the risk that non-state actors will become nuclear-armed. This is a different but related concern to the role that non-state actors such as A.Q. Khan and his network may play, legal or otherwise, in state-based proliferation. The issue of greatest concern is that non-state actors — individuals, companies, cities, or non-states (secessionist movements, theocracies) — may seek and obtain WMD capabilities.
As is well documented, ideological and criminal networks originate in as well as cross through all the countries of East Asia.38 North Korea has been highlighted as a potential source of dual-use or of nuclear weapons-specific knowledge, material, skills, or hardware due to its combination of supply (of nuclear commodities) with its established proclivity to conduct drug, arms, and other contraband smuggling.39 Taiwan is another “black hole” where such transactions have occurred,40 however, and the existence of nuclear fuel cycles in all countries of the region creates a nuclear security control problem that is universal.41
Post-Fukushima Spent Fuel Vulnerability
In addition to the rise of non-state smuggling, threats, and acquisition of nuclear weapons, the Fukushima nuclear disaster highlights the vulnerability of nuclear facilities to non-state attack, as well as to the diversion of nuclear materials by non-state actors. Fatal design flaws in boiling water reactors (BWR) in Japan and elsewhere became evident. They included:
- Locating spent fuel ponds and reactors at a coastal site subject to massive tsunamis without establishing sufficient defenses to avoid the plant being overwhelmed and destroyed;
- Placing the spent fuel ponds at the top of reactor containment buildings to minimize the core-pond transfer distance and the handling cost and errors (thereby making access to the ponds very difficult in a crisis involving radiological release from the reactor cores);
- Using active, powered cooling systems for spent fuel ponds that have common failure modes with the reactors, thereby leading to loss-of-coolant-induced melting of spent fuel in the ponds and reactors, resulting in the generation of hydrogen and the subsequent explosions that devastated the Fukushima containment buildings;
- The ad hoc use of fire trucks and sea water to provide coolant to spent fuel ponds and reactors that ultimately exacerbated the cooling problem via salt deposition on fuel rods and salt build-up in the ponds and reactor cores;
- Packing increasing amounts of fuel onto racks in spent fuel ponds due to “constipation” (lack of immediate capacity caused by technical and political delays) in the off-site spent-fuel processing and waste storage and disposal systems in Japan. The resulting crowding and heat generation from tightly packed ponds made it even harder to cool the spent fuel rods;
- Using insufficiently strong structures and support for the spent fuel ponds themselves. As a result of less-than-robust design, the spent fuel pools may have cracked due during earthquake and tsunami-related stresses, leading to leakage of radioactive water into the containment building.
Some of these lessons apply to all kinds of reactors; some are BWR-specific. A complete accounting of the failure pathways and design problems at Fukushima will not be available for years. The Fukushima reactor disaster has not yet fully played out, as the reactors and spent fuel ponds remain far from stabilized. Site stabilization and recovery, including dismantlement of the broken spent fuel ponds and reactor cores, will likely take ten to thirty years.42
Meanwhile, a huge quantity of radiation has been released in gaseous, particulate, and liquid forms, and a 40 km exclusion radius has been established around the reactor site.43 No one knows how badly contaminated the land is and therefore when, if ever, the residents of this area who survived the tsunami and earthquake will be allowed to return and rebuild their shattered lives.
There will be many lessons for Northeast Asia to take from Fukushima. One of the most important is how brittle the spent fuel ponds proved to be to the loss of coolant, especially as a result of co-location with reactors, and that the loss of coolant and subsequent release of radiation could lead to wholesale evacuations of cities and towns on a very large scale. In this sense, Fukushima was a “wet run” at what could happen not only after a technological failure or malfunction, but as a result of a malevolent attack on a nuclear facility by a state or non-state actor, or as a result of terrorist diversion of spent fuel and its subsequent use to threaten or attack concentrated populations or military targets.44
In such an attack, one might also expect — as occurred at Fukushima — a set of unpredictable consequences and concatenating effects caused by the initial accident. For example, wildly contradictory statements made by authorities about radiation levels at the site and in the exclusion zone amplified the risks perceived by residents and government agencies. Furthermore, forced electricity outages in the form of rolling blackouts were implemented to conserve power. These outages in turn led to accidents, medical malfunctions, and other problems, but were abandoned relatively quickly, in part due to reduced economic activity and electricity use in the wake of the earthquake, but also because consumers conserved in a self-organized manner to reduce peak electricity demand by an estimated 3 gigawatts almost immediately after the accident. Additional evidence of these concatenating impacts included ripple effects on the global economy due both to the tsunami and earthquake damage and to the implementation of the radiation exclusion zone which shut down critical component plants for a variety of global industries, particularly the automotive and electronic.
Finally, the culturally- and historically-determined fear of radiation due to the Hiroshima and Nagasaki experience, which affected the Japanese response to the Fukushima accident, and the recent history of scandal and cover-ups in the nuclear sector, particularly at the Tokyo Electric Power Company, the operator of the Fukushima reactor-complex, shook the public’s trust that the accident would be resolved. In all these ways, Fukushima demonstrates and provides insight into the range of possible impacts of a successful attack on radiological targets such as spent fuel ponds.
Concern about nuclear facilities as radiological targets began with discussions of targeting these sites during the Cold War to “enhance” the effects of nuclear strikes. An early debate occurred over the risk of nuclear terrorism in light of Theodore Taylor’s work on the topic.45 The first public systematic treatment of the issues associated with targeting nuclear facilities by terrorists (by Bennett Ramberg) included the targeting of spent fuel ponds and other ancillary facilities that support reactors, but concentrated on the risk of attacks by states on reactors and the consequent radiological risks.46
In the United States, non-governmental researchers, especially scientists, have been at the forefront of research on the risks posed by poorly-protected and badly-designed spent fuel ponds in reactor containment buildings, putting pressure on the Nuclear Regulatory Commission to respond with limited but significant success to date.47 These experts raised the risk that non-state actors could attack spent fuel ponds and casks at reactor sites. They estimate quantitatively and qualitatively the truly immense, catastrophic possible releases that could result from successful attacks.48 In some cases, a simple repositioning of casks could reduce the risk and impacts of attacks substantially. Some redesign of storage casks could also greatly reduce the risks that a successful non-state actor could breach such spent fuel containers.
Importantly, the Massachusetts Institute of Technology (MIT) Future of the Nuclear Fuel Cycle study, for which an update was released in March 2011, strongly recommended that spent fuel be stored in a central repository, noting that “requirements for on-site spent fuel management may increase and design basis threats may be elevated” because of the Fukushima disaster.49 Due to the expanded risk of radiological contamination from attacks on dry casks or spent fuel ponds located outside the reactor building but co-located with reactors, it appears necessary to consider separating dry cask storage, at least surface storage, from reactor sites. This relocation would ensure failure in either reactor or storage technology due to accident, malfunction, or malevolence does not lead to disablement by contamination of the adjacent facility.
Such spatial rearrangement of spent fuel storage on-site at various types of power reactors, and from reactors to centralized sites, entails costs, but it could also increase vulnerability to possible state and non-state diversion and/or attack on such storage. Ironically, so long as the spent fuel ponds were contained inside the reactor containment building, they were somewhat secured by the facility security systems from armed attacks by non-state actors, although various modes of non-state attack such as crashing aircraft into reactor buildings on the 9/11 model still posed a conceivable threat to these enclosed ponds. The fact that guards were discovered asleep at one American reactor suggests security issues are not always taken seriously.50
Once removed from the reactor building, various cost and design choices need to be made with regard to spent fuel storage and disposition. Each of these choices entails different levels of risk of diversion or successful attack by state and non-state groups. One such choice pertains to the cost and longevity of spent fuel storage technologies. Options include deciding between pools and dry casks, and between dry casks suitable for high-level waste almost straight out of the reactor versus dry casks used only after five or ten years of decay and cooling off, which are therefore less expensive —but also more vulnerable to attack. Other choices include:
- The use of ancillary barriers to reduce the possibility of successful attack on and/or diversion of dry casks in storage on reactor sites;
- The use of surface versus underground storage facilities at reactor sites to reduce the possibility and consequences of land or aerial attack on dry casks;
- The use of various combinations of dry cask storage on reactor sites versus rapid removal of spent fuel to a centralized repository, located either on the surface or underground, that uses either pools or dry cask storage; and
- The selection of choices outlined above in relation to retrievable forms of storage for eventual spent fuel reprocessing versus those designed for medium or longer term irretrievable disposal, such as deep borehole disposal.
These and other design considerations affect the possibility that a devastating radiological attack by a state or a non-state actor could occur by exploiting the measures taken, post-Fukushima, to reduce the reciprocal risk of reactors and spent fuel storage systems, as well as the radiological outcome of a successful attack. The steps taken to reduce reciprocal risk may also affect the probability of successful diversion of spent fuel for use in a dirty bomb or in actual nuclear weapons at another location. Evaluation of alternative disposition of spent fuel must also take the risk of diversion into account to the extent it can be shown to exist at the margins.
States in the region have been dilatory in the extreme in addressing this risk. The Seoul Nuclear Security Summit in March 2012 called for coordination to make this connection between nuclear fuel cycle management, safety, and security, noting, “We affirm that nuclear security and nuclear safety measures should be designed, implemented and managed in nuclear facilities in a coherent and synergistic manner… Noting that the security of nuclear and other radioactive materials also includes spent nuclear fuel and radioactive waste, we encourage States to consider establishing appropriate plans for the management of these materials.”51 Although it called for action to address risks related to the management of spent fuel and wastes, the Summit focused on control of fissile material, did not have a panel on nuclear safety and security, and failed to offer any concrete recommendations for how nuclear facilities should be designed or secured so as to reduce the risk of accident or attack and the attendant radiological consequences of such events. Thus, it appears to have been left to civil society organizations in Northeast Asia to tackle this question directly.52
Even if states succeed in establishing near-perfect control over nuclear facilities and material, controlling the movements of nuclear-capable scientists and technicians is even more difficult. Proliferation activity by non-state actors that does not end up as nuclear weapons activity does not matter in the real world. To move from merely hypothetical to WMD-reality, proliferating states or non-state entities with WMD-nuclear aspirations must obtain scarce expertise in nuclear weapons.
There are no public figures for how many WMD knowledge-endowed and technically capable individuals exist in nuclear weapons and non-nuclear weapon states (NNWS), either globally or in the East Asia region. Often, large global numbers are cited based on American or Russian experience (125,000 personnel is often mentioned for the former Soviet nuclear weapons complex). But in one study of South Africa, the total nuclear weapons workforce was estimated to be quite small, about 400 personnel over the duration of the program (1970-1993). 53 By 1989, the total staffing was about 270, of which about half —or 135 —were estimated to be directly involved. However, other former participants in this program assert that only about ten of these people were truly WMD-nuclear capable and posed a true proliferation risk before the program was terminated in 1989. One, at least, is reportedly under house arrest and the others are reportedly under surveillance in South Africa. Based on his survey of this workforce, Andre Buys notes that “Of the former NEWP personnel that were retrenched the majority (71%) of were “very dissatisfied,” and of the sample (about 40% of the total late period workforce), about 16% had worked overseas; at least one was location unknown.” A study in Russia found a similar level of high dissatisfaction with jobs in its nuclear and missile cities and a proclivity to migrate to better conditions, irrespective of the proliferation risks of potential destination countries.54
In the case of the DPRK, of the 5-10,000 workers in the nuclear-industrial and military complex related to nuclear weapons, a similarly small number of truly nuclear-capable individuals, perhaps up to 200, reportedly exist. Larger numbers likely exist in China’s nuclear weapons complex. States with latent nuclear weapons capabilities — South Korea, Japan, and Taiwan — also have many scientists and technicians who could work on nuclear weapons and related delivery systems.
Another consideration is the difficulty of deterring acquisition, deployment, threatened use, and actual use of nuclear weapons by non-state actors, especially if they are not connected to any particular place or state. One taxonomy of non-state actors includes what Brad Roberts calls jihadi movement-networks:
foot soldiers; the terrorist professionals who provide training and other logistical guidance and support; the leaders of al Qaeda; groups affiliated by ideology and aspiration (so-called franchisees); operational enablers (financiers etc.); moral legitimizers; state sponsors; and passive state enablers (generally weak states that are unable or unwilling to prevent terrorists from exploiting their territory or other assets).55
To this list, Daniel Whiteneck adds the “larger societal sponsors (networks of financiers, supporters, scientists, smugglers) of nuclear terrorism,”56 and then expands this taxonomy to include more moderate, less ambitious, or more risk-adverse terrorist groups, or groups competing for the same constituencies. These groups might be influential within terrorist networked movements with a propensity to adopt nuclear weapons strategies. They are, therefore, potential subjects of strategies aimed at inducing them to exercise a restraining influence over the more nuclear weapons-oriented networked movements.
From the global, regional, and local perspectives, other types of non-state actors must be differentiated. These include “homegrown” loners or groups in “target” countries; ideologically motivated insurgencies, separatist movements, free-floating and self-generating terrorist cells and cults; alienated or corrupt officials or disaffected or unemployed scientists; unaffiliated, non-ideological and for-profit and -hire opportunist suppliers (corporate, criminal, diasporic); corrupt, incompetent, or alienated officials (border agents, intelligence agents in states of primary origin of nuclear weapons, having facilities and dual use capabilities that can be diverted, or in states of potential nuclear weapons transit, deployment, and actual targeted delivery-detonation); and leaders and operatives of state sponsors of controlled, arms-length or disavowable non-state networked movements.
The impossibility of controlling a large number of diverse, self-organizing agents, especially individuals and ideologically motivated networks with top-down control strategies orchestrated by states, suggests fundamental issues of vulnerability may drive urban forms and building designs that provide greater resilience against possibly inevitable nuclear threats and even attacks by non-state actors in the coming decades. The trend in major cities is exactly the opposite, towards even bigger primary and secondary cities with gigantic urban corridors emerging between these mega-cities. But, as noted in chapter 2, there is also an opposite trend of in-situ and networked urbanization known as “rurbanization“ in India and desakota in China and elsewhere in Asia, which may prove less vulnerable.
After the risks of nuclear next-use between states in a universally nuclear-armed East Asia, especially attacks aimed at populations, the risk of nuclear next-use by non-state actors may be the second most important source of risk — not the least because it could vastly complicate inter-state conflicts during times of high tension or even in the midst of war.
Grappling with the Complexity of Nuclear Weapons in East Asia
This section examines three types of strategies to reduce and eliminate these types of nuclear next-use risk. These are state and market-based solutions, regional networked solutions, and civil society-based solutions.
The primary state-based means to contain nuclear weapons proliferation are a combination of international treaties and conventions that establish the basic framework of nuclear and non-nuclear weapons states under the NPT and the closely related system of safeguards run by the International Atomic Energy Agency and related regional safeguards systems. These are supplemented by ad hoc UN Security Council resolutions that mandate national sanctions against proliferating states, their officials, and corporate and non-state entities involved in their proliferation activities. This system of direct regulation by nations is supplemented by the Proliferation Security Initiative, an ad hoc coalition of states organized by the United States and intended to interdict illegal shipments of nuclear weapons-related hardware or material.
These global regimes are supplemented in many regions by nuclear weapons-free zones (but not in East or Northeast Asia), by specific bilateral or national declarations such as the 1992 Denuclearization Declaration of North and South Korea, and the 1968 Three Non-Nuclear Principles of Japan. More recently, another ad hoc mechanism was instigated by the George W. Bush Administration, the “Six Party Talks” devoted to denuclearizing North Korea. However, no regional security mechanism exists in the region, and prospects are dim for a state-based institution emerging in the near future.57
In the case of past proliferation activity, primarily on the part of its own allies, namely South Korea and Taiwan, the United States exerted considerable leverage by threatening to reduce military aid while offering financial support for expanded nuclear power programs. However, the solutions adopted in both instances — no reprocessing or enrichment allowed — contrasts strongly with the treatment accorded to Japan by the United States, which agreed in 1979 to allow the latter to build enrichment and reprocessing plants after blocking the same in South Korea in 1975. This consequently gave rise to a discriminatory and inherently unstable system of state-based restraints on nuclear fuel cycle activities in the two American allies that persists to this day.
With regard to adversarial proliferation by North Korea, the United States first enlisted the former Soviet Union to induce North Korea to join the NPT and to accept safeguards. After North Korea was discovered out of compliance with its safeguard’s declaration, they attempted from 1992-2004 to bilaterally compel and to some extent induce North Korea to reverse direction and to denuclearize.58 As is well known, these efforts, most importantly in the form of the Korean Peninsula Energy Development Organization, failed, and the Bush Administration treated North Korea with malign neglect and then malign engagement, leading rapidly to North Korean nuclear testing in 2006 and again in 2009, and the subsequent collapse of the Six Party Talks.
Another possible approach that rests heavily on states cooperating for common security is the creation of a regional nuclear weapons-free zone (NWFZ). To date, restrictions on nuclear deployments have been established in Japan and the two Koreas (now abandoned in the North), and the United States withdrew all its forward-deployed tactical and theater nuclear weapons from the region in 1992.
Four different zonal concepts have been examined since the end of the Cold War, all at the behest of security intellectuals and social movement activists. The first by a study group led by John Endicott tested the idea of a limited nuclear weapons-free zone. It would cover part of the territory of the nuclear weapons states (NWS) in the region (that is, China, Russia and the United States) and therefore some of their intermediate-range nuclear forces, as well as the territory of the three then non-nuclear states (NNWS) in the region, the two Koreas and Japan.59 Aside from the obvious asymmetries that made negotiating such a treaty difficult, as well as likely problems with monitoring and verification of the status of nuclear forces in the nuclear weapons states, the eruption of the North Korean nuclear weapons tests in 2006 and the subsequent strategic bifurcation of Northeast Asia into states aligned with China versus those aligned with the United States (with Russia on the sidelines) made the concept obsolete.
The second concept was developed in Japan, specifically by the peace researcher Hiromichi Umebayashi and by Peace Depot, a civil society activist and research organization, which was influential in political circles in Japan, especially with the former Foreign Minister Katsuya Okada in 2010.60 They based their approach on the notion of three non-nuclear weapons states — the two Koreas and Japan — receiving a guarantee from the nuclear weapons states of non-use of nuclear weapons against the non-nuclear states. However, this concept has also been shunted aside by the DPRK’s nuclear breakout.61
The third concept was advanced by Morton Halperin in 2000. It is similar to the Umebayashi concept, but proposes to include Taiwan, either by incorporating it into the treaty as a non-state (not done in any other nuclear weapons-free zone to date) or through a side agreement between China and Taiwan. Essential to Halperin’s concept is the simultaneous adoption by the United States of a no-first use policy with regard to nuclear attack on the one hand, and the notion that Taiwan also be covered by the zone on the other — a legal and political question that unless addressed could lead to China refusing to participate in the zone.62
The fourth concept proposes that Japan and South Korea should not wait for North Korea to disarm and fully denuclearize. Instead they should proceed apace to create a bilateral nuclear weapons-free zone, thereby either leaving the DPRK isolated but with the door open for its later entry or inviting it to join from the outset as a non-compliant party — much as occurred with Brazil and Argentina when the Latin American Treaty of Tlatalelco was signed on the basis of differentiated entry.63 Separately, the NWS would calibrate their no-use against NNWS party to the Zone treaty to the extent to which they are denuclearized, that is, as a function of the DPRK’s incremental disarmament.
The crux of this idea is to create an institutional mechanism that “captures” the DPRK’s breakout and creates a stabilizing framework to avoid further nuclear risk-taking behavior in areas of high tension, such as Korea in 2010. The Six Party Talks were to have created such a security mechanism in Northeast Asia but failed. Instead, a six party treaty would take its place as the enduring institutional security mechanism in the region. It is premised on the hypothesis that the DPRK really wants a legally binding treaty commitment of non-use of nuclear weapons against it. And, even the negative security assurance offered in the latest American Nuclear Posture Review (2010), should the DPRK disarm, would not cut the mustard because it is only an executive-branch and not a sovereign commitment, let alone a commitment in effect backed by the other nuclear weapon states that would be party to a NWFZ treaty.64
Finally, one partly market-based strategy for reducing nuclear insecurity has also been proposed, variously called PACATOM and ASIAATOM. The notion is to create regionally integrated nuclear fuel cycles, either at the front-end through an enrichment consortium that would offer increased security of supply in all participating countries, in return for which enrichment would not be undertaken anew in any non-nuclear country, or at the back-end through cooperative management of spent fuel and nuclear waste disposal. To date, none of these market-based schemes have moved from concept to implementation, partly due to asymmetries of corporate capacity and interest, concern to maintain proprietary technology and market shares, and cost. Some form of regional cooperation seems inevitable, however, if only to ensure long-term secure and sustainable separation of nuclear wastes from the biosphere — an imperative underscored by the radiological exposures imposed by the Fukushima disaster. Of particular salience is the potential for “deep borehole” direct disposal of nuclear wastes in Northeast Asia.65
The Role of Civil Society in Networked Governance over Nuclear Weapons Threats
Contrary to conventional wisdom, at least among security analysts focused on Northeast Asia, David Shambaugh has argued:
The core actor in this area is not the nation-state, but a plethora of non-state actors and processes — many of which are difficult to measure with any precision — that operate at the societal level. These multiple threads bind societies together in complex and interdependent ways. Indeed, they point up another significant way in which the Asian region is changing: its traditional geographic subcomponents — Northeast Asia, Southeast Asia, South Asia, Central Asia, and Oceania — are no longer useful intellectual constructs for dividing or distinguishing the macro processes occurring throughout the region.66
Moreover, as he points out, this interdependence is accelerating, and in itself deters conflict and creates resources that can be used to maintain peace and stability in each conflict zone. In Northeast Asia, these non-state actors and processes are still relatively weak, even nascent. Transnational civil society networks in this region, constituted largely by cosmopolitan, multilingual, and highly mobile younger elites, do not themselves create a security community — an urgent priority even from a purely military perspective.67
Nonetheless, these networks already play multiple roles in resolving security issues in the region, including in relation to the threat of nuclear next-use. Many organizations and individuals have played important roles in convening Track 1.5 and Track 2 dialogues with North Korea, for example. Others have gone where states cannot go and implemented actual development projects inside the DPRK to plant the seeds of future cooperation and improved mutual understanding between the antagonists in the Korean conflict.
Civil society organizations and intellectuals outside of the state and market have also developed important security agendas to be addressed by states — such as the nuclear weapons-free zone concept outlined in the previous section — but also in terms of building the local foundations of cooperative security at the community level. Thus, local governments have coordinated development projects across borders, even across the Korean Demilitarized Zone, and have begun to promote networked sharing of sustainable and secure communities regardless of national borders.
Civil society organizations have a long tradition in this region of promoting human rights, opposing military dictatorships, evicting nuclear weapons forward-deployed by great powers, and pushing for nuclear weapons-free zones. This critical tradition is likely to continue in the future on a more transnational and instantaneous basis due to modern connectivity. This enables civil society networks to swarm around rapidly emerging security problems, even in the midst of war or near-war, as happened in South Korea after the Cheonan incident in March 2010, when the South Korean government found itself unable to act decisively in part due to the international mobilization of critics of its anti-North Korean stance on the sinking of the ship.
Social Media and Security Issues in China
Almost unnoticed by the world of analysts focused on state-based security issues, a new factor has erupted onto the strategic landscape in Northeast Asia — the rise of the Chinese “netizen” with access to Chinese social media. This new voice — or scores of millions of voices — adds a new layer of complexity to regional security issues that affects not only the Chinese leadership, but also the calculus of external players, whether they are states or non-state actors of various kinds.
Among China’s security and foreign elites, different policy currents may diverge over core domestic issues of political reform versus democracy. But when it comes to shared notions such as China’s rightful place in the world, the nature of external threats, and the appropriate geostrategic response — including nuclear and conventional force structures — these elites converge on the status quo. The policy currents that shape China’s national security and foreign policy orientations are relatively insulated from direct pressure from a range of societal entities in Chinese society. External information flows to and from officials are channeled via bureaucracies and are, to some extent, controlled. Well-known gatekeepers meet and extract various rents from external visitors at these points of entry and control, whether they are official Track 1.0, semi-official Track 1.5, or non-official, non-state Track 2 foreign entities and individuals coming to China to engage. The currency of rent may be financial in the business world, but in the security and foreign policy domain, it is often kept in cumulative guan-xi accounts through which Chinese officials extend assistance to outsiders and expect reciprocity in the future — the basis of the intensely personal, networked and fluid forms of power that are the core of modern Chinese politics.68
Both the inner and outer circles of this national security and foreign policy-making elite are highly Internet-connected. Even here, however, Chinese security analysts must tread carefully to ensure that what they write abroad does not transgress what they can say at home. They must self-censor or be edited by domestic publishers in any media. Nonetheless, these elite analysts clearly read what is published by their international counterparts, many of whom have invested much effort in mapping China’s institutional terrain and listing the key personnel and entry points for information flows in these relatively well-understood organizations.69
Today, however, China’s rapidly emerging civil society is already a significant factor affecting China’s security policy. Many foreign policy and security issues, including nuclear weapons-related security issues, are spilling into or arising from within China itself. Many of these issues lead to a massive social response. They bear directly on domestic agendas that determine the stability of the rule of the Chinese Communist Party, or the relative power of local, provincial, and central governments, especially on economic, social equity, and ecological issues. As with all ruling parties, maintaining power and stability are at the top of the hierarchy of institutional imperatives. Undoubtedly, the bulk of popular use of the Internet and social media concerns relatively apolitical and low-level issues that do not bear directly on the high politics of national security and foreign policy. Official censors and self-censoring by Chinese security analysts ensure that will remain the case for the foreseeable future.
Nonetheless, there is much “space” for open discussion of domestic and international issues. Empirical studies by Yang have documented that China’s social media focuses on distinct themes: popular nationalism, rights defense, corruption, and manipulation of how the “netizens” (people active in online communities) of China use virtual media to collectively comment on or criticize official policies and actions. Here, the scale shifts from some thousands of officials who make security and military policy, and with whom one might purport to relate via face-to-face visits or systematic distribution and promotion of Internet services, to a wholly different order of mass communication, unprecedented in human history, involving millions of contributors and consumers of on-line media conversing almost instantaneously and often without warning.
Before we examine such on-line civil society, first we must note the extraordinary speed and breadth of individual connectivity to the Chinese Internet. At the end of 2012, China had about 560 million Internet users.70 By 2015, this figure will double breathtakingly to about 1.1 billion users of Internet-connected digital devices, or about 87 percent of the projected population. The biggest expansion will be that of digital devices used in social media.
The use of email, micro-blogs, and social media over smart phones and tablets operates at a velocity and scale in China that is qualitatively and quantitatively new. Social media in China is a vast electronic landscape, but it revolves around two Weibo platforms. These are Tencent and Sina, each of which has about 500 million subscribers, although it is unclear how much the memberships overlap.
Also, the typical Chinese netizen is not simply absorbed in private or domestic concerns. A significant level of virtual and often virulently critical commentary now exists on “core” foreign policy and security issues, much of it highly critical of the central government and its policies. In Table 5.3, we present a selection of social media “storms” that relate to foreign policy and security issues, including China-DPRK relations and Japan’s military white paper.
Undoubtedly, some of the nationalist and even xenophobic positions articulated in China’s popular social media are encouraged by officials and official agencies to buttress the central government’s position in dealing with external adversaries such as the United States, Japan, and even the DPRK. This is evident in the case of their response to Japan’s white paper in 2013. Typically, however, although some bloggers (often officials in private capacity) support government policy, the vast majority of China’s netizens are critical or even condemnatory of government policy when the case calls for outrage (as in the case of the DPRK arrest of a Chinese fishing vessel).
Table 5.3: Selected Social Media Commentary On Security Issues, 2012-2013
|
January 2012, Rumors of DPRK Coup: Chinese netizens mostly dismissed as “implausible” rumors of a DPRK coup d’état. February 2012, Rumors of North Korea Assassination Attempt: PRC netizens discussed a rumor that DPRK leader Kim Jong-un was assassinated in his house in Pyongyang. April 2012, PRC-DPRK Account Gains Following: Pro-North Korea “Today Korea” account opened on Sina Weibo and attracted over 100,000 followers in only a few days. September 2012, Anti-Japan Protests Become Hot Topic: Anti-Japan protests related to Sino-Japanese territorial disputes over the Senkakus (Diaoyu Islands in China) discussed on Chinese social media. April 2013, PRC Netizens Report Military Mobilization on DPRK Border; Oil Aid Unaffected: Despite foreign media reports that China suspended crude oil exports to the North in February, Sina Weibo user “Chaoji Da Benying” said that the operation of the oil pipeline from Dandong to North Korea appeared to be undisrupted (1 April). “RyanEquilibrium” claimed to see DPRK “officials” at an oil measurement station in Dandong, which the user said was visited every month (1 April). • User “mickeymouse” said in a posting on local forum Dandong Fengyun Wang that Dandong Customs officials turned a blind eye to oil products carried by trucks “travelling to North Korea daily” (24 March). May 17-24 2013, DPRK Seize Chinese Fishing Boat: PRC netizens commented on May 5 seizure by DPRK of a Chinese fishing boat and its crew. Most condemned the DPRK for the abduction, calling the country “ungrateful.” • Noting that it is not the first such seizure, Hu Xijin, editor-in-chief of Huanqiu Shibao (Global Times) called the captors “a bunch of scoundrels” and suspected that the DPRK had its own people in Dandong. (Sina Weibo, 20 May). • Retired Major General Luo Yuan, vice president and secretary general of the China Council for the Promotion of Strategic Culture, expressed anger over the incident, saying the DPRK had “gone too far” (Sina Weibo, 20 May). • Responding to the release of the fishing boat and its crew, PRC diplomat nicknamed “Vegetarian Cat 2011” opined that there were “no winners” and that both sides were “losers” (Sina Weibo, 20 May). When DPRK special envoy Choe Ryong Hae arrived on 22 May, soon after the release, most rejected the visit, calling the DPRK “shameless” and “ungrateful.” QQ Weibo user “Wang Yong Liang” called the DPRK “shameless,” criticizing Choe for “having the nerve to come and ask for money” and urged China to stop giving aid (QQ Weibo, 23 May). Sina Weibo user “Zheng Yu 2011” asserted that China should “stand firm” and show its “determination to denuclearize the DPRK.” (Sina Weibo, 23 May). Calling the DPRK an “ungrateful wolf,” user “TimeU, Qing Tu Yin Xu” maintained that the DPRK is “useless” to China and that Choe only visited China to “seek protection and food” (Sina Weibo, 23 May). June 2013, PRC Netizens Discuss Japan’s Defense White Paper: PRC microblogs Sina Weibo and QQ Weibo posted 11,938 and 7,800 comments on Japan’s defense white paper, which accused China of attempting “to change the status quo by force based on its own assertion.” Bloggers on Jiefangjun Bao’s official weibo criticized Japan for “playing up the China threat” and “creating tensions and conflicts” (QQ Weibo, 10 July). Most condemned Japan for its ambitions and said its “ultimate goal” is to “break away” from the United States. Sina Weibo user “Bu Jian Zheng,” for example, maintained that Japan is only “using” the United States and that it is “biding its time to stab the United States in the back” (Sina Weibo, 10 July). Sina Weibo user “Qiao Xin Ting Xue” urged China to “speed up” its process of bolstering the military (Sina Weibo, 10 July). July 2013, PRC Microbloggers on Li Yuanchao’s Presence at DPRK’s Armistice Day Events: While some microbloggers such as Sina Weibo user “Di Daren” (Sina Weibo, 29 July) argued that in view of Japan’s threat, China must ally with the DPRK, others such as Sina Weibo user “nta” criticized Chinese Vice President Li Yuanchao’s 25-28 July visit to the DPRK to mark the 60th Korean War Armistice anniversary for “aiding a tyrant to do evil” and “assisting the Kim dynasty to prolong its dictatorship” (Sina Weibo, 27 July). Another QQ Weibo user called “Blue” wrote, “Wallowing in the mire with the DPRK! Why do we have to commemorate the most terrible war that should not have happened?” (QQ Weibo, 27 July) |
Sometimes, the virtual commentary directly punctures the legitimacy of existing central government foreign policy. It also resonates widely within segments of the e-literate elites, shaking the ideological foundations of policy lines and, in some instances, threatening to sweep away or at least severely erode whole policy lines. China’s alliance with and support for the DPRK is a case in point. In Table 5.4, Chinese social media commentary on the DPRK’s extraordinary nuclear threats against the United States and South Korea in the March-April 2013 period were unreservedly critical not only of the DPRK (“a dog that bites the ones who feed it”) and the United States (which deserves to be “attacked by other countries”), but also of China itself (the crisis is “entirely of China’s own making” and the result of China’s “conniving behavior” toward the DPRK).
Thus, high-level officials, especially younger leaders who are strongly connected to the Internet and to social media, are alert to early signs of “Internet events” like these that activate Chinese super-bloggers (those with more than a million followers) and stimulate social media to swarm all over an issue. (Internet events are “public events with the participation of netizens, which are entities or persons that are actively involved in online communities expressing their opinions or giving comments.”71) The presence of their own avatars and virtual names is an important status symbol of modernity and leadership to many of the younger officials who participate in social media. Due to the pervasive nature of connectivity, this virtual presence includes officials in provincial governments with international borders and those in major trading cities exposed to flows to and from the external world of people, trade, and finance — not just those at the center of power in Beijing.
Exactly how social media plays out in the power dynamics of foreign policy and geo-strategic decision-makers is opaque. On a cultural level, Chinese officials in the academic and policy advisory inner circles often float a trial balloon by mentioning a concept or proposal and saying they heard it from a foreign source if the idea is deemed too controversial or if it is unclear how the idea might be received. The risk posed by raising new ideas can be diluted even further by qualifying the post to the effect that the blogger is only relaying an idea attributable to another party, especially from overseas.
Conversely, even at the very center — the Party’s International Affairs Division — younger officials have been observed proudly reporting their aggressive, even emotional stances on various high profile issues gripping social media, their private voices publicly venting views that are clearly at odds with official policy. These statements are often made in the presence of older and traditional charismatic leaders from an earlier era who carry unquestionable organizational and political authority. Undoubtedly this dissonance has many dimensions. At times, the younger official’s avatar may be using an international post as permission to discuss an issue in China and set agendas. An official’s private avatar may be voicing a trial balloon in policy terms, testing the waters or pushing an alternative policy on highly visible social networks viewed by the personal networks of younger officials connected to him by cohort, mentor, origin, or family. In some cases, these positions even may be encouraged by a silent opponent in order to push an official across a line of permissible versus non-permissible contention with official policy in an attempt to trap the official as part of a line struggle within or across agencies and between policy currents. At some point, the party leadership will deem officials who become serious players on social media to be potential threats to their organizational power in the form of personality cults and populist demagoguery — a possible reason for Bo Xilai’s downfall. Unsurprisingly, therefore, while the Chinese Communist Party and media entities such as Xinhua and People’s Daily have social media accounts in China, senior leaders do not.
The massive reach of super-bloggers in China should not be underestimated. In July 2013, for example, ten Chinese super-bloggers were invited to tour and blog in South Korea — trips that undoubtedly required central government approval.72 Two of these ten have a combined social media following of 23 million Chinese. If only half read their posts, then 11.5 million active followers were exposed to their posts from South Korea. Assuming just two percent of active followers re-tweeted these messages, then the 230,000 re-tweets may have reached a further 1.1 million readers (assuming 500 followers for each of these re-tweeters)! Therefore, just two of the ten super-bloggers likely reached 13 million plus followers in China, demonstrating the huge potential for communication.
Table 5.4: Netizens Respond To DPRK Nuclear Threats, April-March 2013
|
April 4-11, 2013, PRC netizens were observed to comment on the DPRK’s recent warning of a “merciless, sacred, retaliatory war” against its neighbors and the United States… As of 11 April on the popular PRC microblogs Sino Weibo and QQ Weibo, approximately 2,389,173 and 1,347,200 postings were observed respectively to discuss the DPRK’s threat to wage what DPRK KCNA termed a “merciless, sacred, retaliatory war” on its neighboring countries and the United States. Lu Shiwei, a senior researcher of the Institute of Modern International Relations at Tsinghua (Qinghua) University, contended that “the US sanctions, pressures, and isolation against the DPRK for the past few decades” are “one of the root causes of the conflict on the Korean Peninsula” (Sina Weibo, 10 April). Yue Gang, renowned military commentator and former colonel of the PLA General Staff Department, opined the United States had “gone too far” and that “its losses will outweigh its gains” if it decides to make war “with a country that possesses nuclear weapons.” Conjecturing that the United States and the ROK will make certain compromises with the DPRK, Yue maintained that the DPRK will become the “big winner” if no war is launched in the end (Sina Weibo, 9 April). Military expert Zhao Chu asserted that the reason the DPRK had managed to stay “safe” since the Cold War was not due to its nuclear weapon capabilities. Rather, it was because of (1) the complicated situation on the Korean Peninsula, (2) the ROK’s inability to reunite with the DPRK, and (3) former US President George W. Bush’s focus on fighting terrorism (Sina Weibo, 8 April). Many PRC netizens remarked that China was responsible for the current crisis on the Korean Peninsula. QQ Weibo user “Du Qiu” said that China had “raised a dog that bites the ones who feed it,” adding that the DPRK will “destroy” China’s “stability” and the “good progress of the country’s reform and opening up” (QQ Weibo, 10 April). QQ Weibo user “Zhai Cheng Feng” condemned China for double standards, as it “did not say a word” when the United States and the ROK were conducting military drills near the DPRK, but then attacked the DPRK for launching a nuclear test (QQ Weibo, 10 April). Sina Weibo user “Cool Is My Trademark” argued that the current Korean Peninsula crisis “has much to do with China’s conniving behavior” toward the DPRK. Another user, “ItsRyaning,” maintained that the crisis is “entirely of China’s own making” (Sina Weibo, 10 April). Other PRC netizens, however, blamed the United States for the current situation. QQ Weibo user “Stroll in Rainy Night” said that while it was “necessary” for the DPRK to “put up a front,” it was “impossible” that the DPRK would conduct a missile launch unprovoked. He then urged people to “stop chastising only the DPRK,” which behaves the way it does because it has been “pushed into a corner by the United States” (QQ Weibo, 10 April). Sina Weibo user “Mini Young Melon” asked why everyone points their finger at the DPRK but not at the “culprits” – the United States, Japan, and the ROK (Sina Weibo, 10 April). Calling the United States a “nation that does not know how to respect other countries,” Sina Weibo user “Tian Xiang Shan Bu Yong Xue Xi” blamed the United States for the crisis and said it deserves to be “attacked by other countries” (Sina Weibo, 10 April). |
Similar reach can be prompted by external posts circulated inside China. North Korea On the Cusp of Digital Transformation,73 a report on the large-scale adoption and use of cell phones in North Korea and published by the Nautilus Institute on November 1, 2011, went viral on social media in China. On one site,74 the following conversation (summarized after translation) occurs:
A young lady posts a brief excerpt of Nautilus’s North Korea On the Cusp of Digital Transformation. She, her friends, and others chat about it. The first comment is “I had no idea there were so many cell phones in North Korea.” Her friends jump in and start wondering how people can afford cell phones when they can’t eat (a clear indicator that some average Chinese citizens understand North Korea is experiencing a famine). One remarks that a structure is determined by its foundation. And another disparages “Fat Kim / Fat Gold” (in Chinese, the character for “Kim” is “gold”).
Exactly what exposure triggered this netizen interest is unknown. The essay was re-posted by the (official) China Arms Control and Disarmament Association on their website inside China’s firewall on November 4, 2011,75 but social and digital news media did not latch onto it until November 21. Social media interest may have been triggered by international media coverage that mentioned the report on November 21 (a Reuter’s bulletin,76 for example). Perhaps it was domestic digital news coverage that morning (at 163.com, for instance).77 Whether the news media reporters followed the path of social media swarming around the topic or social media were set off by the news media is unclear but also unimportant.
What is evident is that an external report triggered social and news media storms that fed off each other, resulting in massive coverage of a topic highly salient to sensitive external relationships between China and the Koreas, and China and the United States. Consequently, “Internet events” on social media have profound bottom-up and sideways potential to pressure central government officials and agencies to change policy, realign provincial or local government policy, scapegoat a specific individual, company, or agency, etc., in order to preserve the legitimacy and power of the central government or its provincial agents. For example, in the blame game that ensued after the horrific July 2011 crash of a high-speed train in Wenzhou city in Zhejiang Province, Beijing officials used the Internet to put the onus on lax local government and the line agencies responsible for the accident, keeping the focus away from the center.78
One can only conjecture exactly how these information vectors based on virtual, bottom-up citizen mobilization intersect with the personal, intimate politics of networked patronage and mutual obligation at the center. One answer is to argue that such influence can only be inferred indirectly from observed effects, always subject to the problem of counter-factuality (what else might have changed or been influential, which can never be known in full). Another answer is to use either formal or informal agent-based modeling to simulate the true complexity of this interplay and then interpret the patterns that result from the specification of the agents and their decision rules.
For example, using agent-based modeling, Tan, Li and Mao simulated two public Internet events in China in 2010: the Synutra baby milk powder scandal and the conflict between Qihoo and Tencent software companies over privacy protection software.79 In both cases, Internet events erupted and resulted in hundreds of reports, scores of thousands of comments, and, ultimately, government intervention to resolve both situations.
The model specified five entities: main party, opposite party, netizen group, media, and government. The main party refers to the people or the group who initiate a hot event. The opposite party is the group which has interests regarding the event that conflict with the main party. Their actions usually trigger the Internet event. The netizen group is the netizens who are associated with the Internet event via online participation. Media refers to traditional mass media. Government is assumed to be an intermediary in some respects in this model, rather than the primary target of netizen ire.
Each of these five parties has one or more “belief states” (for example, that of government is concern and its own credibility) affected by interaction during the Internet event. Each also has a set of possible actions. Government actions, for example, are to get involved, judge the winner, appease, award, punish, and not to respond. Each of these has an associated estimate intensity and target. Interactions between the entities are governed by rules that specify how the actions of one entity influence the others. Thus, when conflicts increase between the main and opposite party, media and netizen concern also increases. Actions by other parties such as netizen criticism also increase the concerns of all parties. Often, negative actions (in the case of netizens, these include to praise, donate, digitally broadcast or suppress, and criticize) have more influence than positive actions, which is reflected in the models.80
Tan, Li, and Mao used a standard agent-based modeling tool (Repast) to represent these entities, states, and interactions and compared their interaction over time with actual social media data mined from postings. In the case of the Synutra, the skepticism and anger of the netizens clearly contributed to the media attention and eventual government intervention after official inaction and cover-up.81 The simulated pattern of interaction over time closely, but not always, matches that of the actual data — as in the modeling of the Qihoo and Tecent conflict. Of particular interest is the way that social media and mass media coincide in putting the main party in the Internet event, and thereby the government, in a negative limelight that forced official response.
In a foreign policy or national security context — especially one involving high levels of secrecy such as nuclear weapons policy, deployments, threats, delivery systems, or outcomes of use — a relatively simple five agent model such as that above may be difficult to specify, but not impossible. In some cases, the object of ire may be a local embassy of a target main group (for example, as occurred with protests against Japan in China in recent years). At present, we are not aware of any agent-based modeling of the interaction of social media with elite perceptions, views, and policy-making in China.
Nonetheless, we are always free to infer how social media influences officialdom and vice versa, starting with the fundamentals and taking into account the contextual and structural parallels between domestic Internet events and official policy with foreign policy and national security concerns. As noted earlier, contending Chinese policy currents that transect China’s pyramid of power (composed of the party, military, and line agencies) confront a set of “master narratives” about domestic and international issues that frame modern China. In terms of the legitimacy of power at the center, these policy currents propose different approaches to the primary issues of the distribution of wealth and power, equity and social justice, political reform and democracy, ecological integrity, and the fate of the oppressed minorities. When such issues explode into Internet events, they provide an opportunity for central authorities to monitor local developments, to direct ire against local agencies, or to promote local solutions to concrete local social problems. Bottom-up reporting of local events, combined with expression of local resentment, are amplified by social media into Internet events and enable the center to be responsive to social grievances in a long tradition of petitioning for redress against local abuses of power and authority. The Internet and social media become a means whereby Chinese citizens can participate in deliberations within China’s rigid political system, thus avoiding the structural changes required to create a democratic, pluralist system.
In some of the key concepts that legitimate Communist Party rule, such as restoring China’s rightful place in the world,82 national security and foreign policy concerns loom large. In the case of North Korea, for example, the explosion of social media commentary on DPRK issues and its sensitivity to the latest rumors, as well as field reporting along the border, included at various times strongly stated views concerning China’ diminished prestige, its (lack of) ability to impose its will on its small but nuclear-armed ally, and its passive role relative to the United States in coercing the DPRK to capitulate on nuclear and other issues. This time, the social media commentaries coincided with a policy line struggle that continued for months in Beijing as to whether to demote the DPRK from a full alliance to a marginal and possibly negative relationship in the context of regional and global geo-strategic considerations.83
In this instance, social media not only criticized core tenets of Chinese policy towards the DPRK, including its emphasis on slow reform before regime change. It also focused directly on previously taboo topics for public discussion, such as the nuclear weapons issue arising from the DPRK’s campaign of nuclear threats against the United States and its allies, and even, some admitted, against China itself. We summarize the breadth and depth of this discussion in Table 5.4. Similar sentiments and debates to those expressed in social media were observed within the foreign policy and security elite at the center. In some cases, officials used the stereotype of ugly North Koreans to whip up nationalist sentiment (as in the fishing boat incident). But in general, Chinese virtual opinion and much of the central officialdom have shifted their emotional and political loyalties away from an alliance born in the blood of 900,000 Chinese casualties in the Korean War towards eventual cutting adrift the North Korean ingrates. There are also generational fault lines: those who were directly involved in the Korean War as Chinese People’s Volunteers fighting in Korea have been out of power for almost a decade, while the e-literate elites are present at most levels of government and account for almost all provincial and municipal level leaders. The China-DPRK alliance holds, but remains strictly based on brutal self-interest without regard to emotional and ideological ties forged during the Korean War.
The points at which social media form flash floods that feed into tributaries that, in turn, merge into slower moving policy currents down-river are chaotic and indeterminate. Sometimes social media will be driven by central government policies, statements, and actions and accelerate a bottom-up or sideways push effect. In other instances, social media will amplify pressure building in a policy current to the point that it can burst through resistance and lead to change instigated at the highest level, often by the replacement of senior officials. The ultimate flood, a burgeoning social movement demanding democratic pluralism, faces a massive dam — the Party. But all sorts of billabongs, holding reservoirs, spillways, and other devices exist to forestall the day when virtual deliberative discourse would contribute to sweeping away the dam represented by the Party’s monopoly on political power.
Overall, the always shifting edge of the chaotic interplay between personalized, networked politics at the center and massive social media mobilization increases the volatility and turbulence of policy making processes, not least because social media accelerates the propagation of errors and thereby increases uncertainty. Top-level officials and political figures are driven by this dynamic to seek ever-broader social and political bases in order to share risk and diversify their sources of legitimacy — and to demonstrate the breadth of their support.
Observable trends in social media may affect how this interaction takes place. Already, Chinese social media have begun to establish “rumor refutation” groups, such as weibo piyao in 2010. Others have created “self-purification” networks dedicated to exposing fake or false information, in part to offset the amplification by social media of erroneous field reporting or rumor propagation associated with Internet events.84 This self-corrective feature of social media combined with more reflective, less event-driven posts may herald the emergence of a mature civil society in China able to address national security and foreign policy issues in ways that are more amenable to uptake and to policy reformation at the center.
Social media in China allows nascent civil society to have a voice, albeit only a limited voice, in the expression of values and views that are incorporated into China’s foreign policy and security policies. Although constrained, social media may play an important supplementary role to the state and to market entities in terms of situational awareness, self-surveillance, and direct regulation of behavior in time-critical situations that arise from non-state populations in the first place — such as criminal networks moving drugs, trafficking in humans, or smuggling nuclear weapons-related knowledge or items. Many of the leaders of Chinese social media, including elite security analysts and officials, already network with external parties and receive constant infusions of information and analysis in spite of the Great Firewall.85 How these new players affect China’s foreign policy and security calculus is a critical variable in future security challenges confronting its neighbors and competitors. In this regard, civil society networks which communicate directly and effectively with social media in China may be far more influential in shaping China’s policies than governments, especially on security conflicts in which governments are at loggerheads.86
Conclusion
In this respect, therefore, we have already entered a post-hegemonic era in which the foundations of US nuclear hegemony are already so corroded, and its failure to contain North Korean proliferation so obvious,87 that American reassurances increasingly have little meaning to ordinary citizens in allied countries such as South Korea or Japan, or may even evoke opposition to continued alliance. The many cross-border integrative processes that follow from the globalization of culture, economy, and technology — especially massive urbanization — make state-based nuclear deterrence strategies obsolete and absurd. By mid-century, the absurdity of targeting people and places with weapons of mass destruction may become so evident that the fixation of state leaders on gaining nuclear weapons will be viewed as a strange detour in an already archaic past: a time when humans put the very biosphere on which they rely for daily survival at risk of nuclear conflagration, all in the search for deterrence of aggressive intentions that, for the most part, may have never existed in an immediate sense.
For most of the nuclear weapons era, the policies and postures of states have been immune to social movements and civil society. There were significant exceptions, for example, when nuclear weapons were forced out of Japan in 1960 by anti-government protestors, out of Okinawa in 1971 due to popular revulsion to nuclear weapons in Japan, off US surface warships by protestors from the Nuclear Free and Independent Pacific Movement, out of the Philippines and New Zealand due to the rise to power of anti-nuclear advocates in the 1980s, and out of South Korea in 1991 after the overthrow of the military dictatorship in 1987 by the democratic movement.
Soviet nuclear forces were almost completely unaffected in this entire period by civil society, a situation which remains largely unchanged since the end of the Cold War. Chinese and North Korean nuclear weapons programs were also state-based, although they were more implicated in nuclear nationalism than in the other two nuclear weapons states in the region and were therefore more “populist” in ideological terms.
In the era of globalization and transparency, such exclusively state-based nuclear weapons programs are increasingly not viable. Networks of civil society groups dedicated to realizing peace, green agendas, non-nuclear futures, democracy, and human rights will increasingly demand accountability from nuclear weapons establishments and national leaders. Secrecy is always relative, and even the most reclusive, closed states now find themselves ambushed by non-state organizations wielding state-of-the-art surveillance techniques such as satellite imagery, crowd-sourced field reports, and open source intelligence analysis. These networks also produce visions of nuclear disarmament that they propagate via networks across borders, establish deep roots at the local government and city level (as in the 800-strong Mayors for Peace in East Asia), and promulgate new norms and shared practices on nuclear security issues, such as the operation of nuclear fuel cycle facilities. In this manner, civil society organizations have demonstrated great potential to span borders and fill structural holes in Northeast Asia, thereby expanding social capacity to respond to the increasing complexity of the nuclear weapons challenge in this region.
1 Morgan, P.M., Deterrence Now (Cambridge: Cambridge University Press, 2003).
2 Arbatov, A. and Dvorkin, V., The Great Strategic Triangle, The Carnegie Papers (Moscow: Carnegie Moscow Center, Carnegie Endowment for International Peace, 2013).
3 Ochmanek, D. and Schwartz, L., The Challenge of Nuclear-Armed Regional Adversaries (Santa Monica: RAND Corporation, 2008).
4 Allison, G., “Confronting the Specter of Nuclear Terrorism,” ANNALS of the American Academy of Political and Social Science, 607 (Special issue) (2006), doi: http://dx.doi.org/10.1177/0002716206290912
5 Gormley, D.M., Missile Contagion: Cruise Missile Proliferation and the Threat to International Security (Santa Barbara: Praeger Security International, 2008).
6 Anton, P.S., et al., The Global Technology Revolution, Monograph Reports (Santa Monica: RAND Corporation, 2001); National Intelligence Council, Disruptive Civil Technologies: Six Technologies with Potential Impacts on US Interests out to 2025 (Washington, DC: National Intelligence Council, 2008).
7 United States Department of Defense, Quadrennial Defense Review (Washington, DC: United States Department of Defense, 2010).
8 Perkovich, G., et al. (2007).
9 Hayes, P. and Tannenwald, N., “Nixing Nukes in Vietnam,” Bulletin of the Atomic Scientists, 59(3) (2003).
10 For an account of this crisis, see Hayes, P., Pacific Powderkeg: American Nuclear Dilemmas in Korea (Lanham: Lexington Books, 1991).
11 Singlaub, J.K. and McConnell, M., Hazardous Duty: An American Soldier in the Twentieth Century (Mandaluyong City: Summit Books, 1991).
12 United States Department of State, Minutes of Washington Special Actions Group Meeting, Washington, August 19, 1976, 8:12-9:15 A.M, Foreign Relations of the United States, 1969-1976, Volume E–12, Documents on East and Southeast Asia, 1973-1976, Document 285 (Washington, DC: United States Office of the Historian, 1976).
13 United States Department of State, Minutes of Washington Special Actions Group Meeting, Washington, August 25, 1976, 10:30 A.M., Foreign Relations of the United States, 1969-1976, Volume E–12, Documents on East and Southeast Asia, 1973-1976, Document 286 (Washington, DC: United States Office of the Historian, 1976).
14 Bracken, P., The Structure of the Second Nuclear Age, E-Notes (Philadelphia: Foreign Policy Research Institute, 2003).
15 Braddock, J.V., et al., Targeting the Soviet Army Along the Sino-Soviet Border (The BDM Corporation, released under US Freedom of Information Act request to Nautilus Institute, 1978).
16 Kroenig, M. and Pavel, B., “How to Deter Terrorism,” The Washington Quarterly, 35(2) (2012), doi: http://dx.doi.org/10.1080/0163660X.2012.665339
17 “Fish Hunting of the North Korean Soldiers,” Korea DMZ, 2001, http://www.korea-dmz.com/en/s/sa/ssa_01_en.asp For a fishing-shootout in May 2010, see CBS/Associated Press, “Shots Fired as North Koreans Cross DMZ,” CBS News, 11 February 2009, http://www.cbsnews.com/stories/2006/10/07/world/main2072358.shtml
18 Cockle, J., “The Army’s Role,” NBC Report, 1998, http://www.hsdl.org/?view&doc=11715&coll=limited
19 Hayes, P. and Bruce, S., “Translating North Korea’s Nuclear Threats into Constrained Operational Reality,” in North Korean Nuclear Operationality: Regional Security and Nonproliferation, ed. by Moore, G. (Baltimore: John Hopkins University Press, 2013), pp. 15-31.
20 Bennett, B.W., “North Korea’s WMD Capability and the Regional Military Balance: A US Perspective,” Korean Journal of Security Affairs, 14(2) (2009). Bennett, B.W., Uncertainties in the North Korean Nuclear Threat, Document Briefing (Santa Monica: RAND Corporation, 2010).
21 Shaplak, D., et al., A Question of Balance Political Context and Military Aspects of the China-Taiwan Dispute (Santa Monica: RAND Corporation, 2009).
22 Kato, C., TED Case Studies: Taiwan Nuclear Waste Exports (NKORNUKE) (Washington, DC: American University, 1977), http://www1.american.edu/ted/nkornuke.htm
23 Shen, D., “North Korea’s Strategic Significance to China,” WSI China Security, 2(3) (2006).
24 On-Fat Wong, J., Security Requirements in Northeast Asia (Madison, University of Wisconsin, 1982).
25 Ibid., pp. 12-14.
26 Ibid., pp. 65-66.
27 Ibid., p. 69.
28 Ibid., p. 78.
29 Ibid., pp. 79-80.
30 Ibid., pp. 80-81.
31 Ibid., pp. 358-59.
32 Ibid., pp. 315-19.
33 Kipp, J., Asian Drivers of Russia’s Nuclear Force Posture (Arlington: Nonproliferation Policy Education Center, 2010).
34 Shelley, L.I., “Trafficking in Nuclear Materials: Criminals and Terrorists,” Global Crime, 7(3-4) (2006), doi: http://dx.doi.org/10.1080/17440570601073335
35 di Nicola, A., “Trafficking in Human Beings and Smuggling of Migrants,” in The Handbook of Transnational Crime and Justice, ed. by Reichel, P. L. (New York: Sage Publications, 2005).
36 Kafchinski, J., Global Counterfeit Trade (George Mason University, 2009).
37 Kaplan, D.E. and Dubro, A., Yakuza: Japan’s Criminal Underworld (Oakland: University of California Press, 2003).
38 Ward, R. and Mabrey, D., “Organized Crime in Asia,” in The Handbook of Transnational Crime and Justice, ed. by Reichel, P. L. (New York: Sage Publications, 2005).
39 Lijun, M., “Study on Problem of Trans-Border Drugs Crimes on Sino-DPRK Border,” Journal of Chinese People’s Armed Police Force Academy (2009).
40 Kassenova, T., A ‘Black Hole’ in the Global Nonproliferation Regime: The Case of Taiwan, NAPSNet Policy Forum (Berkeley: Nautilus Institute, 2011).
41 Bunn, M., et al., Controlling Nuclear Warheads and Materials: A Report Card and Action Plan, Project on Managing the Atom (Cambridge: Belfer Center for Science and International Affairs and Nuclear Threat Initiative, 2003).
42 Tokyo Electric Power Company, Roadmap Towards Restoration from the Accident at Fukushima Daiichi Nuclear Power Station (Tokyo: Tokyo Electric Power Company, 2011). Yasu, M. and Shiraki, M., “Hitachi, Ge Submit Proposal to Dismantle Crippled Fukushima Nuclear Plant,” Bloomberg, 13 April 2011, http://www.bloomberg.com/news/2011-04-13/hitachi-ge-file-proposal-to-scrap-fukushima-dai-ichi-plant.html
43 Hayes, P., et al. (2011).
44 Robichaud, C., “The Consequence of a Dirty Bomb Attack,” The Hill, 12 April 2011, http://thehill.com/blogs/congress-blog/homeland-security/155493-the-consequence-
of-a-dirty-bomb-attack
45 Willrich, M. and Taylor, T., Nuclear Theft: Risks and Safeguards: A Report to the Energy Policy Project of the Ford Foundation (Pensacola: Ballinger, 1974). Taylor was profiled in McPhee, J., The Curve of Binding Energy (New York: Ballantine, 1974).
46 Ramberg, B., Nuclear Power Plants as Weapons for the Enemy: An Unrecognized Military Peril (Berkeley: University of California Press, 1984).
47 Beyea, J., et al., “Damages from a Major Release of 137 Cs into the Atmosphere of the United States,” Science and Global Security, 12 (2004), http://dx.doi.org/10.1080/08929880490464775. Alvarez, R., et al., “Reducing the Hazards from Stored Spent Power-Reactor Fuel in the United States,” Science and Global Security, 11 (2003), http://dx.doi.org/10.1080/08929880309006
48 Thompson, G., Robust Storage of Spent Nuclear Fuel: A Neglected Issue of Homeland Security (Institute for Resource and Security Studies and Citizens Awareness Network, 2003).
49 Kazimi, M., et al., “Postscript,” in The Future of the Nuclear Fuel Cycle (Cambridge: Massachusetts Institute of Technology, 2011).
50 Mufson, S., “Executive Resigns in Storm over Sleeping Guards,” Washington Post, 10 January 2008, http://www.washingtonpost.com/wp-dyn/content/article/2008/01/09/AR2008010903
368_pf.html Holt, M. and Andrews, A., Nuclear Power Plant Security and Vulnerabilities, Report for Congress (Washington, DC: Congressional Research Service, 2008).
51 Nuclear Security Summit leaders, “Seoul Communiqué at 2012 Nuclear Security Summit,” Council on Foreign Relations, 27 March 2012, http://www.cfr.org/proliferation/seoul-communiqu-2012-nuclear-security-summit/p27735
52 Security of Spent Nuclear Fuel (Berkeley: Nautilus Institute), http://nautilus.org/projects/by-name/security-of-spent-nuclear-fuel/#axzz2STq2M8Ed
53 Buys, A., Proliferation Risk Assessment of Former Nuclear Explosives/Weapons Program Personnel: The South African Case Study, NAPSNet Special Report (Berkeley: Nautilus Institute, 2011).
54 Tikhonov, V., Russia’s Nuclear and Missile Complex: The Human Factor in Proliferation (Washington, DC: Carnegie Endowment For International Peace, 2001).
55 Roberts, B., Deterrence and WMD Terrorism: Calibrating its Potential Contributions to Risk Reduction (Alexandria: Institute of Defense Analysis, 2007).
56 Whiteneck, D., “Deterring Terrorists: Thoughts on a Framework,” The Washington Quarterly, 28(3) (2005), doi: http://dx.doi.org/10.1162/0163660054026452
57 Snyder, S., “Envisioning a Northeast Security Framework: The Korean Peninsula,” in Towards a Northeast Asian Security Community: Implications for Korea’s Growth and Economic Development, ed. by Seliger, B. and Pascha, W. (New York: Springer, 2011), pp. 27-38.
58 Morgan, P.M., “Deterrence and System Management: The Case of North Korea,” Conflict Management and Peace Science, 23(2) (2006), doi: http://dx.doi.org/10.1080/07388940600665768
59 Endicott, J.E., “Limited Nuclear-Weapon-Free Zones: The Time Has Come,” Korean Journal of Defense Analysis, 20 (1) (2008), doi: http://dx.doi.org/10.1080/10163270802006305.
60 Hiromichi, U., “Toward a Northeast Asia Nuclear Weapon-Free Zone,” Japan Focus (2005).
61 Hayes, P., “The Status Quo Isn’t Working: A Nuke-Free Zone Is Needed Now,” Global Asia (2010).
62 Halperin, M., The Nuclear Dimension of the U.S.-Japan Alliance, NASPNet Special Report (Berkeley: Nautilus Institute, 1999).
63 Redick, J., A Differentiated Entry into Force Procedure — Precedents and Legacies: Tlatelolco’s Contribution to the Next Century (Agency for the Prohibition of Nuclear Weapons in Latin America and the Caribbean, 1997).
64 Hayes, P. and Hamel-Green, M., “Paths to Peace on the Peninsula: The Case for a Japan-Korea Nuclear Weapon Free Zone,” Security Challenges, 7(2) (2011).
65 Kang, J., An Initial Exploration of the Potential for Deep Borehole Disposal of Nuclear Wastes in South Korea, NAPSNet Special Report (Berkeley: Nautilus Institute, 2010). von Hippel, D. and Hayes, P., Deep Borehole Disposal of Nuclear Spent Fuel and High Level Waste as a Focus of Regional East Asia Nuclear Fuel Cycle Cooperation, NAPSNet Special Report (Berkeley: Nautilus Institute, 2010). Zhou, Y., An Initial Exploration of the Potential for Deep Borehole Disposal of Nuclear Wastes in China, NAPSNet Special Report (Berkeley: Nautilus Institute, 2012).
66 Shambaugh, D.L., “China Engages Asia: Reshaping the Regional Order,” International Security, 29(3) (2004).
67 Blair, D.C. and Hanley, J.T., “From Wheels to Webs: Reconstructing Asia‐Pacific Security Arrangements,” The Washington Quarterly, 24(1) (2001), doi: http://dx.doi.org/10.1162/016366001561393
68 Brown, K., “China: What We Think We Know Is Wrong,” Open Democracy, 15 May 2013, http://www.opendemocracy.net/kerry-brown/china-what-we-think-we-know-is-wrong
69 Chinese Nuclear Arms Control and Disarmament: Principal Players and Policy-Making Processes (Monterey: Center for Nonproliferation Studies, James Martin Center for Nonproliferation Studies, 2009), http://cns.miis.edu/opapers/op15/chart_11x17_china.pdf
70 China Internet Statistics Whitepaper (Singapore: China Internet Watch, 2013), http://www.chinainternetwatch.com/whitepaper/china-internet-statistics/
71 Tan, Z., et al., “Agent-Based Modeling of Netizen Groups in Chinese Internet Events,” Society for Modeling & Simulation International Magazine, 3(2) (2011).
72 Yonhap News Agency staff writer, “Chinese ‘Power Microbloggers’ to Visit S. Korea This Week,” Yonhap News Agency, 1 July 2013, http://www.globalpost.com/dispatch/news/yonhap-news-agency/130701/chinese-power-microbloggers-visit-s-korea-week
73 Mansourov, A., North Korea on the Cusp of Digital Transformation, NAPSNet Special Report (Berkeley: Nautilus Institute, 2011), http://nautilus.org/wp-content/uploads/2011/12/DPRK_Digital_Transformation.pdf
74 The exchange is found in Chinese at http://tieba.baidu.com/p/1292015149
75 Mansourov, A., North Korea on the Cusp of Digital Transformation..
76 Jiawei, Z., “Korean Mobile Phone Users to Reach One Million Four Years after Mobile Phone Ban Lifted (in Chinese),” Reuters, 21 November 2011, http://cn.reuters.com/article/CNAnalysesNews/idCNCHINA-5247520111121?page
Number=2&virtualBrandChannel=0
77 China Daily staff writer, “British Media Says North Korean 3G Mobile Phone Users to Reach One Million,” China Daily, 21 November 2011, http://news.163.com/11/1121/11/7JCM79DL00014JB5.html
78 Xu, X., Internet Facilitated Civic Engagement in China’s Context: A Case Study of the Internet Event of Wenzhou High-Speed Train Accident (Columbia University, 2011).
79 Tan, Z., et al. (2011). Tan et al refer to Tecent, but the proper name (from the website http://t.qq.com/) in English is Tencent, which is used here instead.
80 Ibid., pp. 40-42.
81 Ibid., pp. 42-43.
82 Monitor 360, Master Narratives Country Report: China (Open Source Center, 2012).
83 Jun, J., “Dealing with a Sore Lip: Parsing China’s “Recalculation” of North Korea Policy,” 29 March 2013, http://38north.org/2013/03/jjun032913
84 Xu, X. (2011).
85 In China, online adults fall into the following categories (individuals can be in more than one): creators (40%), critics (44%), collectors (34%), joiners (23%), spectators (71%), and in-actives (25%). See China Social Media Usage (Shanghai: Resonance).
86 Melissen, J., “Concluding Reflections on Soft Power and Public Diplomacy in East Asia,” in Public Diplomacy and Soft Power in East Asia, ed. by J., M. and Lee, S. J. (New York: Palgrave MacMillan, 2011).
87 Hayes, P., The Stalker State: North Korean Proliferation and the End of American Nuclear Hegemony, NAPSNet Policy Forum (Berkeley: Nautilus Institute, 2006).